Introduction
Imagine this: You’re a cybersecurity enthusiast, a system administrator, or even just someone curious about how networks really tick. You’ve run into a situation where a simple ping isn’t enough, or ssh feels too heavy-handed for a quick check. You need a tool that’s agile, versatile, and gets straight to the point of network communication.
Enter Netcat.
Often hailed as the “TCP/IP Swiss Army Knife,” Netcat is a legendary utility in the networking and cybersecurity world. From opening basic connections to transferring files and even listening for incoming data, it’s a foundational tool that every aspiring network professional should understand. Its simplicity belies its immense power, making it indispensable for quick diagnostics, simple data transfers, and even uncovering network vulnerabilities.
In this guide, we’ll peel back the layers of Netcat, exploring its core functionalities through practical scenarios. By the end, you’ll not only understand what Netcat does but also grasp why it’s so incredibly useful in a variety of networking situations.
What is Netcat?
At its heart, Netcat (often abbreviated as nc) is a command-line utility designed for reading from and writing to network connections using either TCP (Transmission Control Protocol) or UDP (User Datagram Protocol). Think of it as a fundamental tool that allows you to establish raw connections, send data, and receive responses directly over a network, bypassing the complexities of higher-level applications.
It’s cross-platform, available on most Linux distributions, macOS, and even Windows (often as nc.exe). You can typically check if it’s installed by typing nc -h or install it on Debian/Ubuntu-based systems with sudo apt install netcat-traditional.
Fundamental Modes of Operation
Netcat primarily operates in two fundamental modes: acting as a listener or acting as a client.
A. Listener Mode (Server)
Scenario: You need to quickly test if a specific port on your machine is reachable, or perhaps you want to set up a rudimentary “receiving station” for some incoming data without setting up a full server.
In listener mode, Netcat “listens” on a specified port, waiting for an incoming connection from another machine. It’s like setting up a simple mailbox that waits for a letter to arrive.
- Command:
nc -lv -p <port>(or often simplync -l <port>on some versions) - Example: Let’s say you want to listen on port
12345.
nc -lv -p 12345
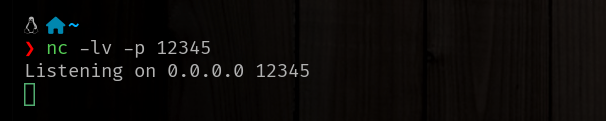
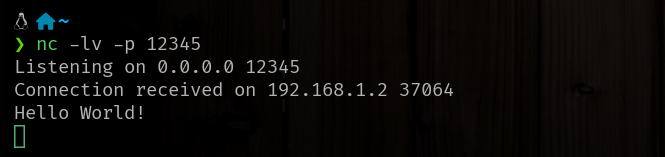
Your terminal will appear to hang, waiting for a connection. Once a connection is made, any data sent from the client will appear in this terminal, and anything you type here will be sent back to the client.
B. Client Mode (Initiator)
Scenario: You have a service running on a remote machine (maybe a simple server you just set up, or a common web server), and you want to connect to it directly to send data or see its immediate response.
In client mode, Netcat initiates a connection to a listening port on a target machine. This is like sending a letter to a specific mailbox at a known address.
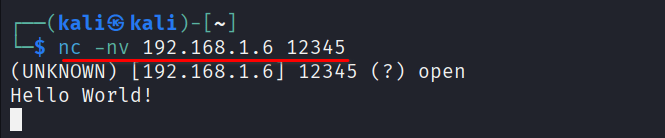
- Command:
nc -nv <target_ip> <target_port> - Example: To connect to the listener we set up at
192.168.1.100on port12345:
nc -nv 192.168.1.6 12345
Practical Applications of Netcat
Netcat’s real power comes from combining these basic modes with various command-line options and standard I/O redirection.
A. Port Scanning
Scenario: You’ve just brought up a new server and need to quickly check which ports are open and responding to connections. Or perhaps you’re investigating a potential security issue and want to see what services are exposed.
While more sophisticated tools like Nmap exist for in-depth port scanning, Netcat offers a quick and dirty way to check for open ports.
- Command:
nc -zv <target_ip> <start_port>-<end_port> - Example: To scan ports 20 through 25 on
example.com:
nc -zv example.com 20-25-z: Tells Netcat not to send any data after establishing a connection; it just checks if the port is listening.-v: Provides verbose output, showing you which ports are open or refused.
B. Banner Grabbing
Scenario: You’re performing initial reconnaissance on a target system or trying to troubleshoot why a service isn’t responding as expected. You want to identify the version of a web server or other network service running on a specific port.
Banner grabbing involves connecting to a port and receiving the initial text (banner) that a service sends, often revealing its type and version.
- Command:
echo "GET / HTTP/1.0\r\n\r\n" | nc example.com 80For HTTP (port 80), you send a basic HTTP GET request. Theechocommand provides the input, piped (|) directly to Netcat.For other services (e.g., SMTP on port 25, FTP on port 21), simply connecting might be enough:nc mail.example.com 25The initial output will often contain the server’s name and version, aiding in your reconnaissance.
C. Creating Reverse Shells
Scenario: (This is a conceptual scenario for understanding, strictly for ethical purposes.) In penetration testing, after gaining initial access to a compromised machine, you might want to establish a persistent connection back to your attacking machine, especially if direct incoming connections are blocked by a firewall.
A “reverse shell” is a powerful concept where the target machine initiates a connection back to the attacker’s machine, effectively bypassing ingress firewall rules. Netcat is famously used to create these.
- Crucial Disclaimer: The creation and use of reverse shells should ONLY be performed in controlled, authorized environments (e.g., your own lab, or during a legal penetration test with explicit permission). Using this technique maliciously is illegal and unethical. This explanation is for educational purposes to understand a common cybersecurity technique.
While Netcat can facilitate reverse shells, the specifics involve combining Netcat with system shells (bash, cmd.exe) and command execution. Due to the sensitivity and detail involved, we will dedicate a separate, in-depth blog post specifically to reverse shells, exploring their mechanics, different types, and how they work. This will allow us to cover the topic with the necessary depth and ethical considerations.
Security Implications
While Netcat is an incredibly useful tool for network testing and administration, its power means it also has significant security implications.
- Malicious Use: Netcat is a favorite tool of attackers due to its simplicity in setting up listeners, transferring files, and creating shells. If a system is compromised, an attacker might deploy
nc.exe(on Windows) or use the nativenccommand (on Linux/macOS) to establish command and control. - Corporate Security Systems: Be aware that the
nc.exebinary (the Windows version of Netcat) is widely recognized by antivirus software and corporate security solutions as a potential threat or malicious tool. Due to its dual-use nature, attempting to install or runnc.exeon a company-issued device for corporate or business use may trigger security alerts and could lead to policy violations. Always consult your organization’s IT security policies before using such tools on managed devices. - Firewall Bypass: As seen with reverse shells, Netcat can sometimes be used to bypass simple ingress firewall rules by initiating connections from the inside out.
- Unencrypted Traffic: By default, Netcat sends data in plain text. This means any sensitive information transferred via Netcat is vulnerable to eavesdropping if not tunneled through a secure channel (like an SSH tunnel).
Final Thoughts
Netcat, despite its age, remains a quintessential tool in the network professional’s toolkit. Its elegance lies in its simplicity and versatility, allowing users to perform a wide range of tasks from basic connectivity tests to more complex data manipulation and reconnaissance.
By understanding its fundamental modes—listener and client—and exploring its practical applications through the scenarios we’ve discussed, you’ve taken a significant step in mastering this networking powerhouse. Remember its capabilities, respect its power, and always wield it responsibly and ethically.
Experiment with Netcat in your own isolated lab environments, and stay tuned for our next post, where we’ll delve deeper into the intricate world of reverse shells!