The Paradox of Privacy and Verification
Have you ever needed to prove something about yourself without revealing the underlying sensitive information? Imagine trying to prove you’re old enough to buy a certain product without showing your exact birthdate, or verifying that you know a password without actually transmitting the password itself across a network. In our increasingly digital world, we constantly face a dilemma: to verify a piece of information, we often have to expose the very data we wish to keep private. This creates significant privacy risks, making us vulnerable to data breaches, identity theft, and unwanted surveillance.
This is where Zero-Knowledge Encryption (ZKE), more accurately referred to as Zero-Knowledge Proofs (ZKPs), steps in. At its core, ZKP is a revolutionary cryptographic method that allows one party, the “Prover,” to convince another party, the “Verifier,” that a statement is true, without revealing any information beyond the validity of the statement itself. It’s a powerful tool that promises to reshape the landscape of digital privacy and security.
In this blog post, we’ll embark on a journey to understand what Zero-Knowledge Proofs are, how they work in a simplified manner, their profound importance, and the exciting ways they are being applied today, from securing blockchain transactions to revolutionizing digital identity. We’ll also touch upon the challenges they face and glimpse into their promising future.
What Exactly is Zero-Knowledge Encryption?
Zero-Knowledge Proofs (ZKPs) are a fascinating concept in cryptography. The “zero-knowledge” aspect is precisely why this technology is so groundbreaking: the Verifier learns absolutely nothing about the secret information itself, only that the statement being made about it is undeniably true. It’s like being convinced that someone has the key to a lock without ever seeing the key or the lock, just observing that the door opens.
Let’s break down the core concept: a Prover wants to convince a Verifier that they know a secret (e.g., the solution to a puzzle, a private key, or their age) without actually revealing the secret itself. The Verifier, in turn, wants to be absolutely sure that the Prover is telling the truth. ZKPs achieve this seemingly impossible feat through a series of interactions (or sometimes, a single interaction in more advanced forms) that allow the Prover to demonstrate knowledge without divulging the secret.
Consider the classic “Ali Baba’s Cave” analogy: Imagine a circular cave with two entrances, A and B, and a magic door in the middle that connects them. Only someone who knows the secret word can open the magic door. The Prover (Ali Baba) wants to prove to the Verifier (the friend) that he knows the secret word, without revealing the word itself.
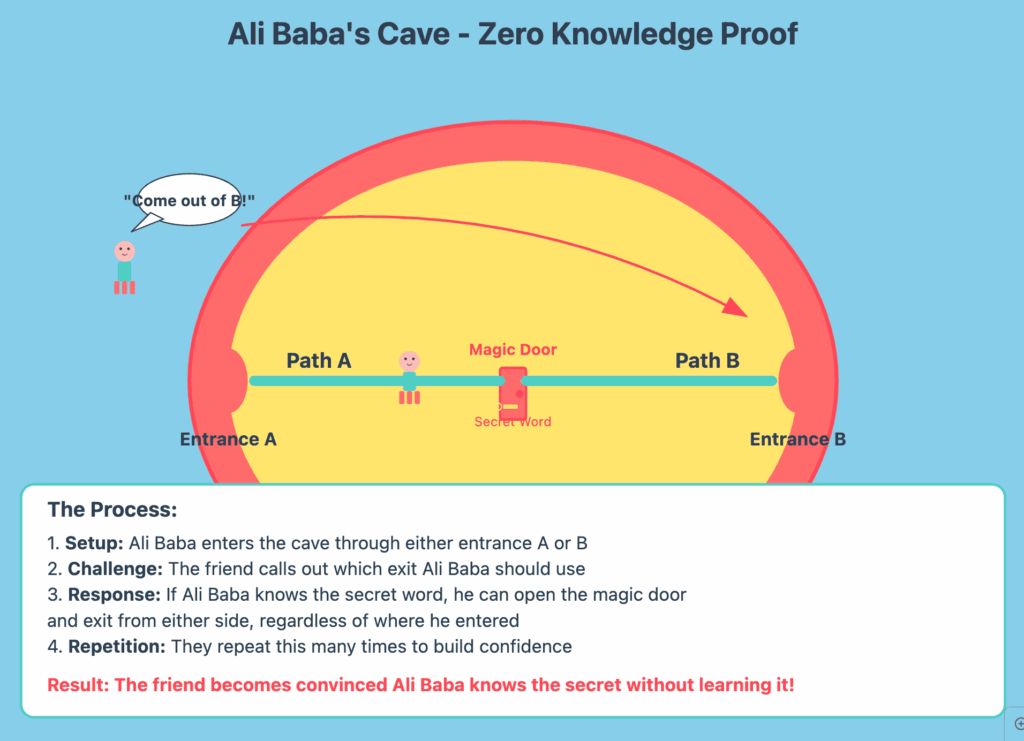
This analogy highlights the three essential properties of any Zero-Knowledge Proof:
- Completeness: If the statement is true (Ali Baba knows the secret word), an honest Prover (Ali Baba) can always convince an honest Verifier (the friend).
- Soundness: If the statement is false (Ali Baba doesn’t know the secret word), a dishonest Prover cannot convince an honest Verifier, except with a negligible probability (the chance of guessing correctly many times in a row becomes astronomically small).
- Zero-Knowledge: If the statement is true, the Verifier learns absolutely nothing about the secret itself (the friend never learns the secret word), only that the statement (Ali Baba knows the word) is true.
How Does Zero-Knowledge Encryption Work
At a high level, Zero-Knowledge Proofs involve an interactive process (though non-interactive versions exist) where the Prover performs a series of cryptographic operations and sends partial information or responses to challenges posed by the Verifier. The Verifier, in turn, checks these responses against the known public information. The magic lies in the fact that these responses, while sufficient for verification, do not leak any information about the secret itself.
While the underlying mathematics can be complex, ZKPs often rely on fundamental cryptographic primitives like hashing functions, public-key cryptography, and mathematical problems that are easy to verify but hard to solve (e.g., discrete logarithms or factoring large numbers).
More advanced ZKP systems, like SNARKs (Succinct Non-Interactive Arguments of Knowledge) and STARKs (Scalable Transparent Arguments of Knowledge), allow for a single, small proof that can be verified quickly without multiple rounds of interaction. These are particularly powerful for applications like blockchain scaling, where efficiency is paramount. While not strictly ZKP, Homomorphic Encryption is a related privacy-enhancing technology that allows computations to be performed directly on encrypted data without decrypting it, offering another layer of data protection.
Why Zero-Knowledge Encryption Matters
The implications of Zero-Knowledge Proofs are vast, offering significant advantages over traditional cryptographic methods:
- Enhanced Privacy: This is the most direct and impactful benefit. ZKPs allow individuals and organizations to prove compliance, verify identities, or validate transactions without ever exposing the sensitive underlying data. This minimizes privacy risks and protects personal information.
- Improved Security: By reducing the amount of sensitive data that needs to be transmitted or stored in the clear, ZKPs inherently reduce the attack surface for malicious actors. If the data is never revealed, it cannot be stolen or misused.
- Trustless Systems: ZKPs enable verification without requiring trust in a third party. This is crucial for decentralized systems, where participants can verify information directly and cryptographically, fostering greater transparency and reducing reliance on intermediaries.
- Regulatory Compliance: With increasingly stringent data privacy regulations like GDPR and CCPA, ZKPs offer a powerful tool for organizations to meet compliance requirements by allowing them to prove data integrity or user consent without revealing the data itself.
- Scalability (for some ZKP types): Non-interactive ZKPs, particularly SNARKs and STARKs, can compress large computations into tiny, easily verifiable proofs. This is revolutionary for systems like blockchains, allowing for a massive increase in transaction throughput while maintaining security.
Real-World Applications and Use Cases
Zero-Knowledge Proofs are moving from academic theory to practical implementation across various industries:
Blockchain and Cryptocurrencies
- Private Transactions: Projects like Zcash utilize ZKPs to enable transactions where the sender, receiver, and amount are all hidden, providing true financial privacy on a public ledger.
- Scaling Solutions (ZK-Rollups): For blockchains like Ethereum, ZK-rollups bundle thousands of transactions off-chain and then generate a single ZKP to prove the validity of all those transactions on the main chain. This dramatically increases transaction speed and reduces fees.
- Identity Verification: ZKPs can allow users to prove they meet certain criteria (e.g., “I am over 18,” “I am a registered voter”) without revealing their full identity details on a blockchain.
Digital Identity and Authentication
- Passwordless Authentication: Users could prove they know a password without ever sending it to a server, significantly enhancing security against phishing and credential stuffing attacks.
- Age Verification: Websites could verify a user’s age without requiring them to upload an ID or reveal their birthdate, protecting privacy while ensuring compliance.
- KYC (Know Your Customer): Financial institutions could use ZKPs to verify a customer’s identity and compliance with regulations without storing sensitive personal documents indefinitely.
Secure Voting Systems: ZKPs could enable voters to cryptographically prove their eligibility and that their vote was counted correctly, without revealing their individual ballot choices.
Supply Chain Verification: Companies could use ZKPs to prove the authenticity of products, the ethical sourcing of materials, or compliance with certain standards, without revealing proprietary trade secrets to competitors.
Cloud Computing: ZKPs can enable secure computation on untrusted cloud servers. A user could prove that a computation was performed correctly on their encrypted data without revealing the data to the cloud provider.
Machine Learning: Researchers and companies could prove that a machine learning model was trained on a specific dataset, or that a prediction was made using a particular model, without revealing the sensitive training data or the model’s proprietary architecture.
Challenges and Limitations
Despite their immense potential, Zero-Knowledge Proofs are not without their hurdles:
- Computational Overhead: Generating ZKPs can be computationally intensive for the Prover, requiring significant processing power and time, especially for complex statements. While verification is often fast, proof generation remains a bottleneck for some applications.
- Complexity: Designing, implementing, and auditing ZKP systems requires deep expertise in advanced cryptography and mathematics. This complexity can lead to higher development costs and a steeper learning curve for developers.
- Proof Size: While SNARKs and STARKs are “succinct,” the proofs generated by some ZKP schemes can still be quite large, which can impact storage and transmission efficiency.
- Quantum Computing Threat: Like many current cryptographic systems, the underlying mathematical problems that secure some ZKPs could theoretically be vulnerable to attacks from powerful quantum computers in the distant future. Ongoing research is exploring quantum-resistant ZKP constructions.
- Adoption and Standardization: As a relatively new and evolving field, ZKPs require wider understanding, developer tooling, and industry-wide standardization to achieve mainstream adoption.
The Future of Zero-Knowledge Encryption
Zero-Knowledge Proofs are poised to become a cornerstone of the next generation of digital privacy and security. Their ability to decouple verification from disclosure fundamentally changes how we can interact with data and digital systems. We are witnessing a rapid acceleration in research and development, with cryptographers continuously finding ways to make ZKPs more efficient, smaller, and easier to implement.
The impact of ZKPs on privacy and security is profound. They hold the potential to reshape how we:
- Manage our digital identities: Giving individuals unprecedented control over their personal data.
- Interact with decentralized networks: Enabling truly private and scalable blockchain applications.
- Securely share and process sensitive information: Fostering trust in environments where it was previously impossible.
As the digital world becomes increasingly interconnected and data-driven, the demand for robust privacy-enhancing technologies will only grow. Zero-Knowledge Proofs offer a powerful answer to this demand, empowering individuals and organizations to build a more private, secure, and trustworthy digital future. Consider the implications for your own data and how ZKPs might soon be silently protecting your information in ways you never imagined.
Final Thoughts
Zero-Knowledge Proofs represent a paradigm shift in cryptography, moving “beyond encryption” to offer a new dimension of data privacy. By enabling us to prove truths without revealing secrets, ZKPs address the fundamental tension between verification and privacy. From revolutionizing blockchain scalability and private transactions to offering novel solutions for digital identity and secure computation, their applications are vast and growing. While challenges remain, the ongoing advancements and increasing adoption of ZKPs paint a clear picture: they are not just a fascinating cryptographic concept, but a vital technology that will fundamentally reshape the future of data privacy and trust in our digital world.