Introduction
In the ever-evolving landscape of web application security, tools that empower developers and security professionals to identify vulnerabilities are indispensable. Among these, OWASP ZAP (Zed Attack Proxy) stands out as a popular, free, and open-source web application security scanner. It’s a powerful, community-driven tool designed to help you find security vulnerabilities in your web applications during the development and testing phases.
What makes ZAP particularly versatile is its ability to operate in various modes, each tailored to different testing needs and user skill levels. Understanding these operational modes is crucial for maximizing ZAP’s effectiveness and ensuring your security testing is both thorough and responsible. This post will explore each of the four primary modes offered by OWASP ZAP: Standard, Safe, Protected, and Attack. We’ll delve into what each mode enables, its key characteristics, ideal use cases, and the pros and cons to help you choose the right approach for your specific security testing scenarios. From automated scanning to manual exploration and controlled attacks, ZAP’s modes provide a flexible framework for comprehensive web application security assessment.
Mode 1: Standard Mode
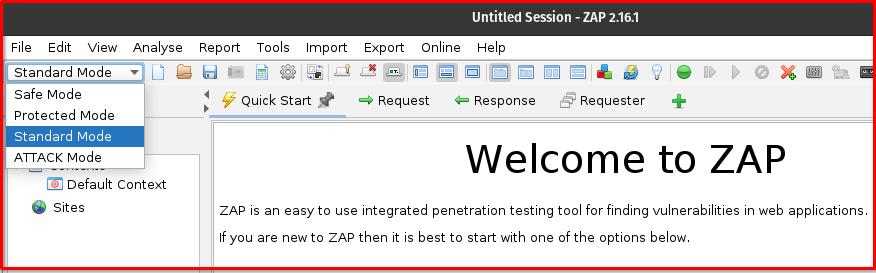
Standard Mode is OWASP ZAP’s default and most commonly used operational mode. When you first launch ZAP, you’ll typically find yourself in this mode, which offers the full spectrum of ZAP’s capabilities without any inherent restrictions.
Key Characteristics:
- Full Functionality Available: In Standard Mode, all of ZAP’s powerful features are at your fingertips. This includes active scanning (which actively probes the application for vulnerabilities), passive scanning (which analyzes traffic without sending new requests), the spider (for discovering application structure), the fuzzer (for injecting malicious data), and many more.
- Allows for Manual Exploration and Automated Testing: This mode provides the flexibility to manually browse and interact with your web application while ZAP passively records traffic and identifies potential issues. Simultaneously, you can initiate various automated scans and attacks as needed.
- Suitable for Both Beginners and Experienced Users: While offering comprehensive control, Standard Mode is accessible enough for beginners learning the ropes of web security testing. Experienced users will appreciate the granular control and access to advanced features for conducting in-depth penetration tests.
Use Cases:
- General Web Application Penetration Testing: It’s the go-to mode for comprehensive security assessments where you need to combine manual exploration with automated vulnerability scanning.
- Detailed Vulnerability Analysis: When you’ve identified a potential vulnerability and need to delve deep, Standard Mode allows you to fine-tune your attacks and analyze responses in detail.
- Learning and Experimenting with ZAP’s Features: For those new to ZAP, Standard Mode is the perfect environment to explore and understand how different features work without any limitations.
- Pros: Flexibility, full control over all ZAP features, comprehensive testing capabilities.
- Cons: Can be overwhelming for new users due to the sheer number of options, requires more manual configuration and understanding of the target application.
Mode 2: Safe Mode
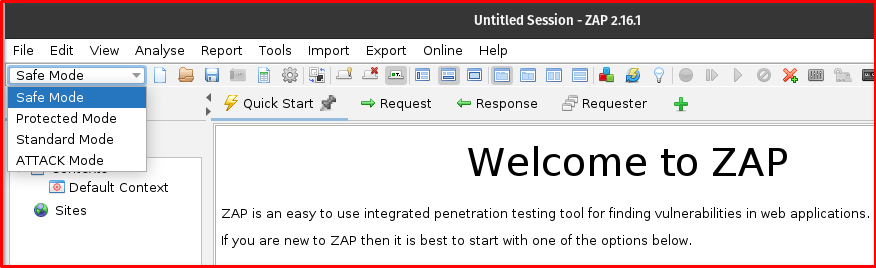
Safe Mode is a restricted operational mode in OWASP ZAP, specifically designed to prevent accidental or potentially harmful actions against your target application. It prioritizes safety and observation over aggressive testing.
Key Characteristics:
- Disables Potentially Dangerous Features: In Safe Mode, active scanning, the fuzzer, and other features that send potentially disruptive or malicious requests to the target are automatically disabled. This significantly reduces the risk of inadvertently affecting a live system.
- Focuses on Passive Scanning and Manual Exploration: The primary focus of Safe Mode is on passive analysis. ZAP will still act as a proxy, capturing and analyzing all HTTP/S traffic that passes through it, identifying passive vulnerabilities and gathering information about the application’s structure without modifying it. You can still manually browse the application.
- Primarily for Observation and Initial Reconnaissance: This mode is ideal for gaining an initial understanding of a web application, mapping its structure, and identifying basic information leakage or configuration issues without any risk of disruption.
Use Cases:
- Testing Production Environments: When testing live production systems where any form of active interference is strictly prohibited, Safe Mode provides a non-intrusive way to perform security checks.
- Initial Reconnaissance and Understanding Application Structure: Before launching any active attacks, Safe Mode allows you to safely map out the application’s attack surface, identify technologies used, and understand its flow without risk.
- Demonstrations or Training: For training sessions or demonstrations where only passive analysis and observation are required, Safe Mode ensures a controlled and safe environment.
- Pros: Enhanced safety, significantly reduced risk of damaging the target application, ideal for sensitive environments.
- Cons: Limited testing capabilities, cannot find vulnerabilities that require active probing (e.g., SQL injection, XSS), provides only a partial security assessment.
Mode 3: Protected Mode
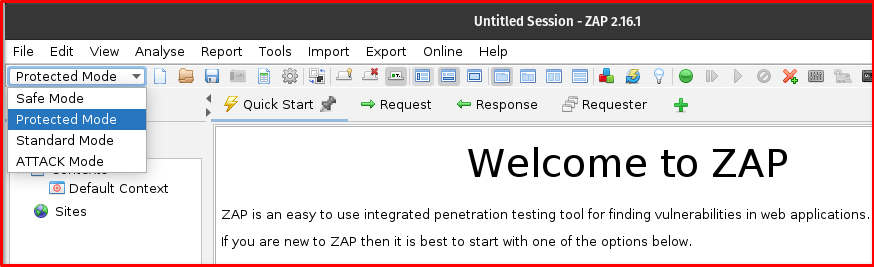
Protected Mode strikes a crucial balance between the unrestricted nature of Standard Mode and the cautious approach of Safe Mode. It allows for active actions, but only on explicitly specified “in-scope” targets, preventing accidental attacks on unintended applications.
Key Characteristics:
- Requires Defining a “Context” and Setting URLs as “In Scope”: To use Protected Mode effectively, you must first define a “context” within ZAP. This context allows you to group related URLs and specify which parts of your application are considered “in scope” for testing.
- Active Actions Permitted Only Against In-Scope URLs: Once a scope is defined, active actions such as active scanning, fuzzing, and other potentially disruptive tests are only permitted against URLs that fall within that defined scope. Any attempt to perform an active action on an out-of-scope URL will be blocked by ZAP.
- Prevents Accidental Attacks on Out-of-Scope Targets: This is the core benefit of Protected Mode. It acts as a safety net, ensuring that your aggressive testing efforts are confined solely to the intended target, preventing collateral damage to other applications or systems.
Use Cases:
- Targeted Testing of Specific Applications or Modules: If you’re focusing on a particular web application or a specific feature within a larger system, Protected Mode ensures your testing efforts are precisely directed.
- Environments with Strict Boundaries: In scenarios where some active testing is allowed, but strict boundaries are necessary (e.g., a shared testing environment with multiple applications), Protected Mode provides the necessary control.
- Team-Based Testing: When multiple testers are working on different parts of an application, Protected Mode helps ensure that each team member stays within their designated testing scope, avoiding conflicts or unintended interactions.
- Pros: Controlled active testing, prevents collateral damage to out-of-scope targets, offers a good balance of safety and testing capabilities.
- Cons: Requires careful and accurate scope definition, can be restrictive if the testing scope changes frequently, initial setup of context and scope can take time.
Mode 4: Attack Mode
Attack Mode is the most aggressive operational mode in OWASP ZAP, designed for rapid and automated vulnerability discovery. It’s characterized by its immediate and continuous active scanning of newly discovered URLs.
Key Characteristics:
- Immediately Launches Active Scans on New URLs: The defining feature of Attack Mode is its automated active scanning. As soon as ZAP discovers a new node (a new URL or resource) in the Sites tree (e.g., through spidering or manual browsing), it immediately launches an active scan against that new entry.
- Designed for Rapid, Automated Vulnerability Discovery: This mode is geared towards quickly identifying common and easily detectable vulnerabilities across a broad attack surface without requiring manual initiation of scans for each new discovery.
- Can Be Very Noisy and Potentially Disruptive: Due to its aggressive and automated nature, Attack Mode can generate a significant amount of traffic and potentially put a strain on the target application. It has the highest risk of causing disruption or denial of service if not used carefully.
Use Cases:
- Testing Non-Production Environments: Attack Mode is best suited for testing environments like development, staging, or dedicated testing servers where aggressive scanning is acceptable and potential disruption won’t impact live users.
- Quickly Identifying Common Vulnerabilities: If you need to perform a rapid initial assessment to find obvious vulnerabilities in a newly deployed application, Attack Mode can accelerate this process.
- Automated CI/CD Pipeline Integration (with caution): With careful configuration and in a controlled environment, Attack Mode can be integrated into continuous integration/continuous deployment pipelines for automated security checks, though this requires robust error handling and monitoring.
- Pros: Speed, high level of automation for active scanning, efficient for broad vulnerability discovery.
- Cons: High risk of disruption or denial of service to the target, can be very noisy and easily detectable, may miss subtle vulnerabilities that require more nuanced testing, should never be used on production systems without explicit permission and understanding of risks.
Choosing the Right Mode
Selecting the appropriate OWASP ZAP mode is paramount for conducting effective, efficient, and responsible web application security testing. Your choice should be guided by several factors:
Factors to Consider:
- Target Environment: Is the application in a production environment, or is it a development/staging instance? This is perhaps the most critical factor, as production environments typically demand a non-intrusive approach.
- Testing Objectives: Are you performing initial reconnaissance, a comprehensive penetration test, or a quick check for common vulnerabilities?
- User Experience Level: Are you a beginner learning ZAP, or an experienced security professional? Some modes offer more control, which can be overwhelming for new users.
- Permissions and Scope of Testing: Do you have explicit permission to perform active scanning? Is there a defined scope for your testing, or are you allowed to test broadly?
General Recommendations:
- Start with Safe Mode for initial exploration, reconnaissance, and understanding the application’s structure without any risk of disruption. It’s perfect for a first look.
- Use Protected Mode for controlled active testing within clearly defined boundaries. This is your go-to when you need to perform active scans but must ensure you only target specific parts of an application or avoid affecting other systems.
- Leverage Standard Mode for full control and comprehensive manual/automated testing. When you need to combine deep manual analysis with targeted automated attacks, Standard Mode provides the ultimate flexibility.
- Employ Attack Mode only in highly controlled, non-production environments where aggressive scanning is explicitly permitted and understood. Never use this mode on live production systems unless you have explicit authorization and are fully aware of the potential consequences.
Final Thoughts
OWASP ZAP’s four operational modes—Standard, Safe, Protected, and Attack—provide a robust and flexible framework for web application security testing. Each mode serves a distinct purpose, catering to different levels of risk tolerance, testing objectives, and user expertise.
By understanding the nuances of each mode, you can strategically choose the most appropriate setting for your current testing scenario. This not only enhances the effectiveness of your vulnerability discovery efforts but also ensures that your testing is conducted responsibly, minimizing any unintended impact on the target application. Mastering these modes is a fundamental step towards becoming a more proficient and ethical web application security tester.
We encourage you to download OWASP ZAP and experiment with each of these modes. Hands-on experience is the best way to truly grasp their power and applicability in real-world security assessments. Happy hunting!