Introduction
In today’s IT landscape, security is no longer optional—it’s a necessity. Whether you are managing a self-hosted blog, a file server, or a complete production environment, protecting your applications from unauthorized access is critical. This is where Authelia, an open-source authentication and authorization server, shines.
Authelia acts as a reverse proxy companion, enabling single sign-on (SSO), two-factor authentication (2FA), and access policies across your applications. Think of it as your security gateway, ensuring only the right people get access to the right services.
🔑 What is Authelia?
Authelia is a self-hosted solution that provides:
- Single Sign-On (SSO): Authenticate once and gain access to multiple apps.
- Multi-Factor Authentication (MFA/2FA): Add an extra layer of protection using TOTP apps (e.g., Google Authenticator) or security keys (e.g., YubiKey).
- Fine-Grained Access Control: Define who can access specific applications based on user groups, IP addresses, or rules.
- Reverse Proxy Integration: Works with popular reverse proxies like Nginx, Traefik, and Caddy.
This makes it ideal for both personal homelabs and enterprise-grade deployments.
🏗 How Authelia Fits in Your Architecture
A common deployment looks like this:
- User tries to access an application (e.g.,
app.example.com). - Reverse Proxy (Caddy, Nginx, or Traefik) intercepts the request.
- The proxy checks with Authelia if the user is authenticated and authorized.
- If not logged in, the user is redirected to Authelia’s login portal.
- Once authenticated, the user gains access according to the defined rules.
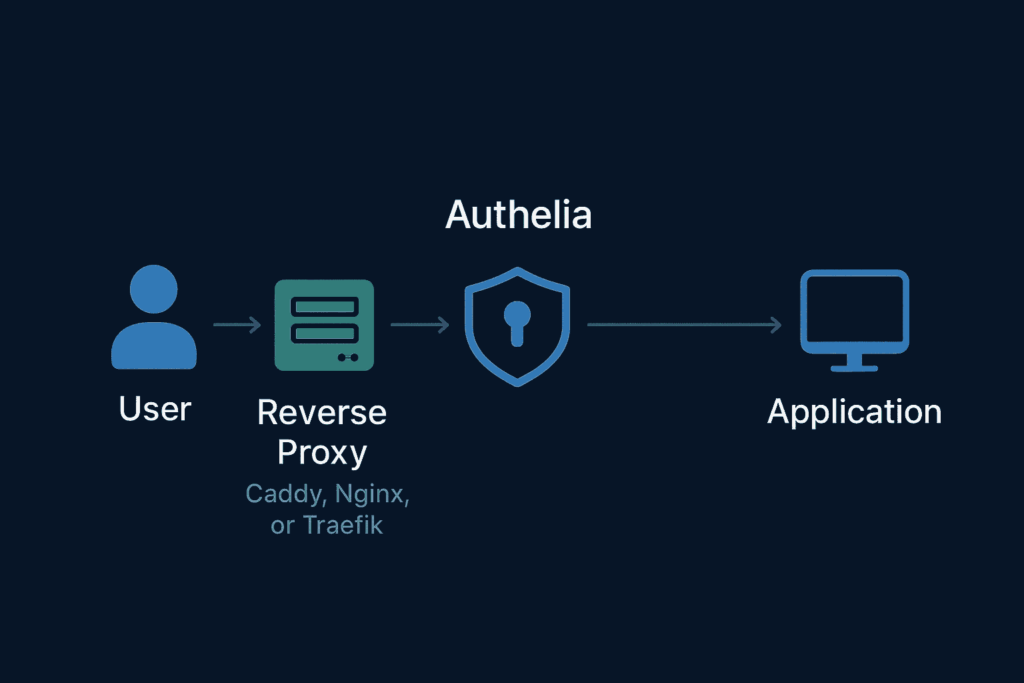
This workflow ensures a centralized security layer, rather than configuring authentication separately for each application.
🚦Demo: Local Caddy + Authelia Dev Stack
Try a local demo combining Caddy (reverse proxy) and Authelia (authentication) using this ready-to-run Docker Compose example:
This repository provides a ready-to-run example for running Caddy and Authelia together on a local machine using Docker. It is intended for development, testing, and learning purposes — not as a production deployment.
🔗 Repository: https://github.com/msfx07/caddy-authelia-Local-Caddy-Authelia-Dev-Stack-
Please follow the “Quick start” section in the repository README.md file to set up and run the demo.
🔒 Why Use Authelia?
- ✅ Centralized Security: Manage access in one place.
- ✅ Flexible Policies: Define access per application, group, or IP.
- ✅ Enterprise-Ready: Supports LDAP, Active Directory, and SAML.
- ✅ Privacy-Oriented: Fully self-hosted, no data sent to third parties.
- ✅ Scalable: Works for both small homelabs and production deployments.
⚖️ Final Thoughts
Authelia bridges the gap between ease of use and strong security for self-hosted and enterprise services. With its robust authentication features and seamless reverse proxy integration, it’s a tool every IT professional should consider for securing their infrastructure.
If you’re running multiple web services—whether for personal projects or business operations—Authelia ensures that only the right users, at the right time, under the right conditions can access your apps.
📖 Further Reading:
Authelia Official Documentation 👉 https://www.authelia.com