Introduction In today's interconnected digital landscape, Application Programming Interfaces (APIs) have become the backbone of modern software architecture. From mobile apps to microservices, APIs facilitate seamless communication between systems, enabling the rich,...
Sandbox99 Chronicles
From My Sandbox to Yours — Practical IT Insights.
Categories: Web Security
API Security 101: DO’s and DON’Ts You Must Know
Introduction As a Security Researcher, I've seen firsthand how critical API security has become in the modern digital landscape. APIs are the backbone of most applications, and their vulnerabilities can expose sensitive data and disrupt services. My journey into this...
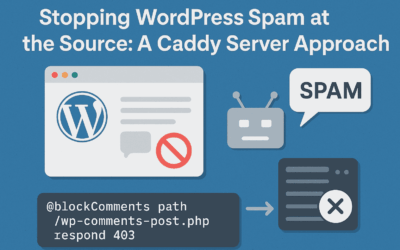
Stopping WordPress Spam at the Source: A Caddy Server Approach
Introduction Many WordPress site owners believe that disabling the comment section from the dashboard is enough to stop all forms of commenting. Unfortunately, that’s not the case. Even with the comment form removed from your pages, spambots can still submit comments...
Stored XSS Explained: A Hands-On Demo with DVWA and OWASP ZAP
🧭 Introduction In this demonstration, we explore one of the most dangerous yet commonly found web vulnerabilities—Stored Cross-Site Scripting (XSS). Unlike its reflected counterpart, stored XSS involves injecting malicious scripts that are permanently stored on the...
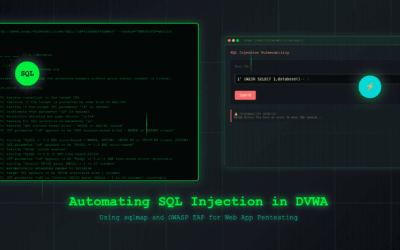
Level Up: Using sqlmap and ZAP for SQL Injection Testing in DVWA
🧨 Introduction In our previous blog post, we successfully demonstrated a classic SQL Injection attack against DVWA (Damn Vulnerable Web Application) using its interactive web interface under security level: low. That exercise helped us understand how vulnerable input...
Testing SQL Injection in DVWA: A Hands-On Tutorial
🛡️ Introduction SQL Injection (SQLi) is one of the most dangerous and commonly exploited web application vulnerabilities. It occurs when an application unsafely includes user input in SQL queries, allowing attackers to tamper with database queries, extract sensitive...