Introduction
Mutillidae II, an intentionally vulnerable web application, stands as a cornerstone in the realm of web security training. Developed by OWASP, it offers a safe and legal environment for individuals to explore common web vulnerabilities, ranging from SQL injection to cross-site scripting, all while enhancing their ethical hacking prowess. Its design, mimicking real-world scenarios, makes it an invaluable resource for students, seasoned professionals, and anyone looking to deepen their understanding of web application security. This guide will introduce you to the power of Mutillidae II and demonstrate how you can leverage Docker containers to create an isolated and efficient sandbox for your security learning journey.
What is OWASP Mutillidae II
OWASP Mutillidae II is a free, open-source, deliberately vulnerable web application designed for web security training and practice. It’s an excellent resource for aspiring and experienced cybersecurity professionals to hone their web hacking skills in a safe and controlled environment.
Here’s a breakdown of what makes it a valuable tool:
Key Features and Capabilities:
- Extensive Vulnerabilities: Mutillidae II contains over 40 vulnerabilities and challenges, covering all of the OWASP Top Ten lists from 2007, 2010, 2013, and 2017. This includes common vulnerabilities like:
- SQL Injection (SQLi)
- Cross-Site Scripting (XSS)
- Broken Authentication and Session Management
- Sensitive Data Exposure
- XML External Entity (XXE)
- Broken Access Control
- Security Misconfiguration
- Insecure Deserialization
- Cross-Site Request Forgery (CSRF)
- Using Components with Known Vulnerabilities
- Unvalidated Redirects and Forwards
- Command Injection
- File Inclusion (Local and Remote)
- Unrestricted File Upload
- And many more!
- Realistic Vulnerabilities: The vulnerabilities in Mutillidae II are “actually vulnerable,” meaning you don’t need to enter any “magic” statements or follow specific contrived scenarios. This makes the learning experience more realistic.
- Learning Aids: It includes built-in hints, tutorials, and even video tutorials to guide users through the exploitation process. You can also toggle between secure and insecure modes to see how vulnerabilities are mitigated.
- One-Click Reset: The system can be easily restored to its default state with a single click, allowing you to practice repeatedly without worrying about breaking the application.
- Multiple Installation Options: Mutillidae II can be installed on Linux and Windows using LAMP, WAMP, and XAMPP stacks. It also comes pre-installed on popular security distributions like Rapid7 Metasploitable 2, Samurai Web Testing Framework (WTF), and OWASP Broken Web Apps (BWA).
- Active Development: The project is frequently updated to maintain relevance and effectiveness.
Use Cases:
- Web Security Training: Ideal for individuals, classrooms, and corporate training courses to learn and practice web application penetration testing.
- CTF (Capture The Flag) Challenges: Can be used as a target for web hacking CTF competitions.
- Vulnerability Assessment Tool Testing: Security researchers and developers can use Mutillidae II to test the effectiveness of their vulnerability scanning tools.
- Ethical Hacking Practice: Provides a safe sandbox for practicing various ethical hacking techniques.
Running OWASP Mutillidae II in a Docker Container as a Sandbox:
Yes, it is absolutely possible and highly recommended to run OWASP Mutillidae II in a Docker container as your sandbox. This is one of the most popular and convenient ways to use it.
Why Docker is ideal for Mutillidae II:
- Isolation: Docker containers provide excellent isolation. This means that if you accidentally “break” or compromise Mutillidae II within its container, it won’t affect your host system or other applications. This is crucial for a deliberately vulnerable application.
- Reproducibility: Docker ensures that the environment is consistent every time you spin up the container, eliminating “it works on my machine” issues.
- Easy Setup and Teardown: You can quickly deploy and remove Mutillidae II with simple Docker commands, making it efficient for lab environments.
- Portability: You can easily move your Mutillidae II setup between different machines as long as Docker is installed.
- Resource Management: Docker allows you to control the resources (CPU, memory) allocated to the container.
How to get started with Docker:
The official OWASP Mutillidae II project provides Docker images and instructions. You’ll typically find options on their GitHub repository or Docker Hub.
Here’s a general outline of the steps (specific commands might vary slightly based on the official image you choose):
Step 1: Launch your Kali Linux Virtual Machine
Step 2: Install Docker and Docker Compose
sudo apt install docker.io docker-compose -y
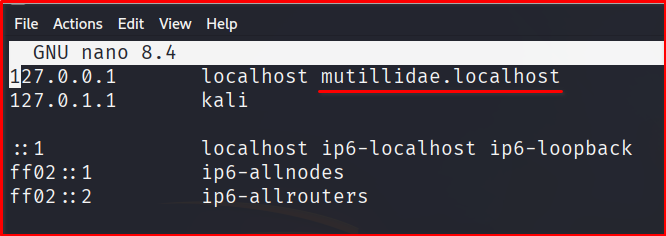
Step 3: Update your /etc/hosts file by adding this multildae.localhost
Step 4: follow the instructions from github by clone the repository and build a docker, minor changes on line 3. I added sudo command and it should be docker-compose when you run it.
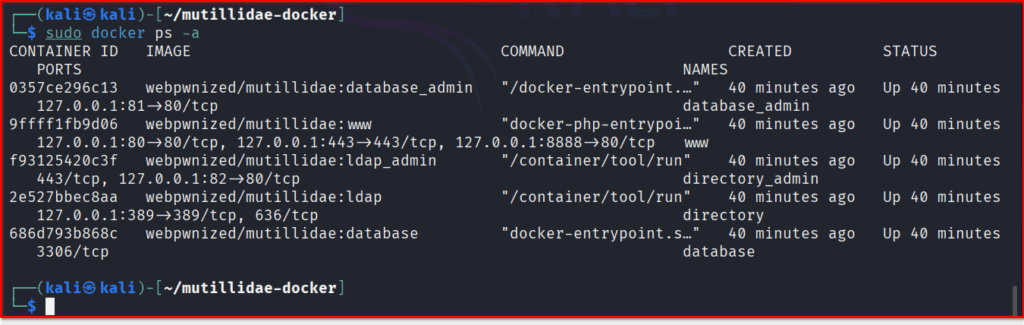
git clone https://github.com/webpwnized/mutillidae-docker.git cd mutillidae-docker sudo docker-compose -f .build/docker-compose.yml up --build --detach
Expect the download and build time for this Docker container to vary with your internet speed and hardware. After running this step, the display should resemble this:
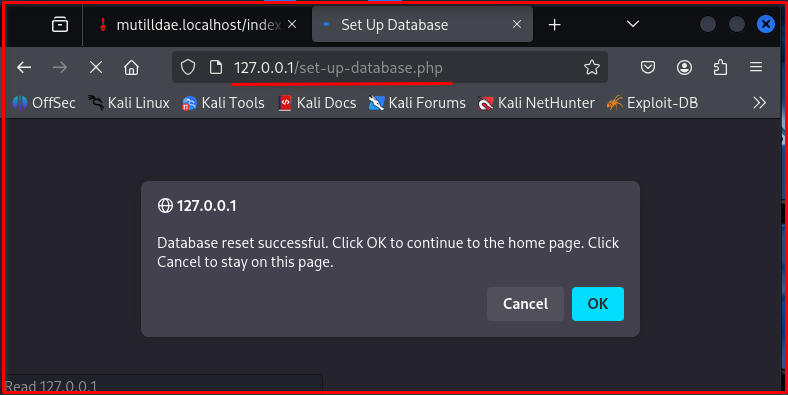
Step 5: Open in browser for database setup.
Step 6: open either in http://127.0.0.1 or http://mutilldae.localhost
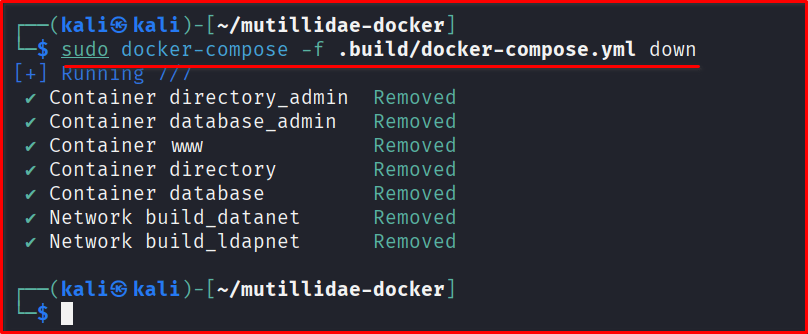
Step 7 (Optional) If you want this to be removed and no longer needed.
sudo docker-compose -f .build/docker-compose.yml down
Important Considerations for your Sandbox:
- Network Isolation: While Docker provides container isolation, consider further network isolation for your sandbox environment. Avoid exposing Mutillidae II directly to the internet. If you need to access it from another machine, ensure proper firewall rules are in place.
- Resource Allocation: Depending on your system and other running applications, you might want to limit the CPU and memory resources allocated to the Mutillidae II container to prevent it from impacting your system performance.
- Regular Updates: Keep your Docker images and Mutillidae II up-to-date to ensure you’re working with the latest vulnerabilities and features.
- Don’t Store Sensitive Data: Since it’s a deliberately vulnerable application, never store any real sensitive data within your Mutillidae II instance.
By leveraging Docker, you can create a highly efficient, safe, and reproducible sandbox environment for practicing your web application security skills with OWASP Mutillidae II.
Final Thoughts
Mutillidae II is a powerful and versatile tool for web security education, offering a comprehensive array of vulnerabilities for hands-on practice. Its design focuses on realism, ensuring that the skills you develop are directly applicable to actual penetration testing scenarios.
The ability to run Mutillidae II in a Docker container is a significant advantage. Docker provides a safe, isolated, and reproducible environment, meaning you can experiment freely without risking your host system. This ease of setup and teardown, combined with its portability, makes Docker the ideal choice for creating your web security sandbox.
By utilizing Mutillidae II within a Docker container, you’re not just learning about vulnerabilities; you’re gaining practical experience in a controlled and efficient lab environment. This combination empowers you to hone your web hacking skills effectively and confidently, preparing you for real-world security challenges.