Introduction
In a world increasingly reliant on digital infrastructure, the battle against cyber threats is constant. But what if there were individuals who could think like the bad guys, without being the bad guys? Enter the world of ethical hacking, a crucial discipline that acts as a proactive shield against malicious attacks.
What is Ethical Hacking?
Ethical hacking, often referred to as “penetration testing,” is the practice of attempting to penetrate computer systems, networks, or applications with the explicit permission of the owner. Unlike malicious hackers who seek to exploit vulnerabilities for personal gain or harm, ethical hackers do so to identify weaknesses and help organizations strengthen their defenses before a real attack occurs.
So, what exactly is the job function of an ethical hacker? An ethical hacker is essentially a cybersecurity professional who simulates cyberattacks to test the security posture of an organization’s digital assets. Their primary role is to identify and report security vulnerabilities, often providing recommendations for remediation. They’re the good guys who actively search for flaws, helping businesses and individuals protect their sensitive data and critical systems. Think of them as the cybersecurity equivalent of a quality assurance tester, but for digital security.
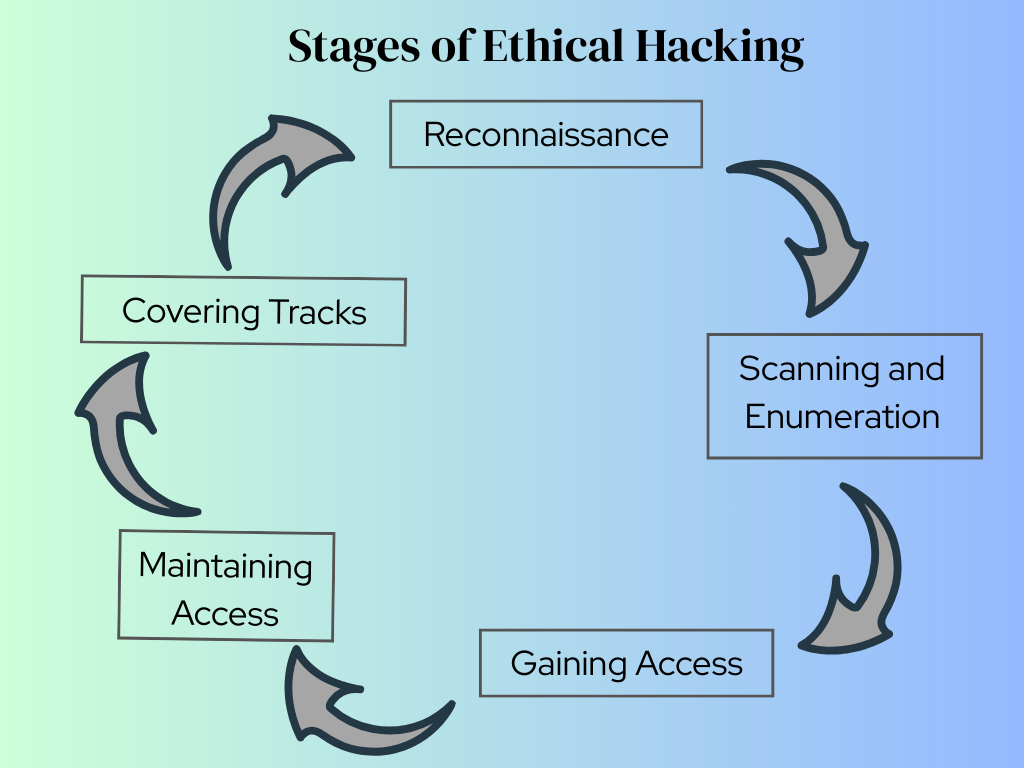
To effectively mimic the tactics of a malicious attacker, ethical hackers follow a structured approach, often broken down into five distinct stages. Understanding these stages is fundamental to grasping the methodology behind securing our digital world.
The Five Pillars of Ethical Hacking
Let’s dive into the five stages that guide ethical hackers in their mission to fortify cybersecurity:
1. Reconnaissance: The Art of Information Gathering
Every successful operation, whether defensive or offensive, begins with thorough preparation. In ethical hacking, this translates to reconnaissance. This initial phase is all about gathering as much information as possible about the target. This can involve:
- Passive Reconnaissance: Sifting through publicly available information like company websites, social media profiles, news articles, WHOIS records, and even Google searches. The goal is to collect intelligence without directly interacting with the target’s systems.
- Active Reconnaissance: Engaging in direct interaction with the target’s network or systems. This might include network scanning to identify live hosts, port scanning to discover open services, or even social engineering tactics (with explicit permission) to gather human-element vulnerabilities.
The more information an ethical hacker uncovers in this phase, the clearer the picture of the target’s vulnerabilities becomes, laying the groundwork for subsequent stages.
2. Scanning and Enumeration: Mapping the Digital Landscape
Once a broad overview is established, the scanning phase narrows the focus. Here, ethical hackers employ specialized tools to systematically scan the target network to identify specific details. This includes:
- Port Scanning: Identifying open ports on a system, which indicates active services that could potentially be exploited.
- Vulnerability Scanning: Using automated tools to detect known security weaknesses and misconfigurations in applications, operating systems, and network devices.
- Network Mapping: Visualizing the network topology to understand the interconnections between different systems and devices.
This stage provides a detailed “map” of the target’s digital landscape, highlighting potential entry points for an attacker.
3. Gaining Access: The Simulated Breach
This is where the rubber meets the road. In the gaining access stage, the ethical hacker attempts to exploit the vulnerabilities identified during reconnaissance and scanning to penetrate the target system or network. This could involve:
- Exploiting software bugs or misconfigurations.
- Cracking weak passwords through brute-force or dictionary attacks.
- Leveraging social engineering to trick individuals into revealing sensitive information.
- Bypassing security controls like firewalls or intrusion detection systems.
The objective here is to successfully breach the system, demonstrating a real-world attack scenario.
4. Maintaining Access: Establishing a Foothold
After successfully gaining access, the ethical hacker moves into the maintaining access phase. The goal here is to establish a persistent presence within the compromised system, simulating how a malicious attacker might try to remain undetected and continue their activities. This often involves:
- Installing backdoors or rootkits for future access.
- Creating new user accounts with elevated privileges.
- Modifying system configurations to ensure continued access.
This phase helps organizations understand the long-term impact of a successful breach and how an attacker might solidify their control.
5. Clearing Tracks: The Ethical Exit
The final and equally critical stage is clearing tracks, also known as “covering tracks.” This is where the ethical hacker meticulously removes all traces of their activity from the compromised system. This is crucial for:
- Ethical Conduct: Ensuring the system is returned to its original state and that no unintended damage is caused.
- Realism: Simulating how a malicious attacker would attempt to hide their presence to avoid detection.
Activities in this phase include deleting log files, removing any installed tools or backdoors, and reverting any configuration changes. This ensures a clean and responsible conclusion to the penetration test.
Final Thoughts
The five stages of ethical hacking — Reconnaissance, Scanning & Enumeration, Gaining Access, Maintaining Access, and Clearing Tracks — form the backbone of a structured and effective penetration test. They provide a methodical approach to uncovering vulnerabilities and strengthening an organization’s cybersecurity posture.
If you’re aspiring to become an ethical hacker in the future, this is a good reference to remember every time you perform your job. These stages aren’t just theoretical steps; they are practical guidelines that will shape your approach to identifying and mitigating cyber threats. Mastering them is essential for any aspiring cybersecurity professional committed to using their skills for good, safeguarding our digital world one ethical hack at a time.
Beyond the Fundamentals: Continuing Your Ethical Hacking Journey
To further advance your expertise in ethical hacking, I encourage you to follow my upcoming blog series. I will delve into specific categories within each of the five stages you’ve learned here, offering in-depth insights, advanced techniques, and practical applications. Referencing these foundational concepts regularly will ensure your methodology remains aligned with industry best practices and a robust security mindset.




