🚀 iptables Essentials: A Beginner’s Guide to Network Security 🔥
Looking to secure your Linux server or network? iptables is a fundamental firewall tool that gives you full control over traffic filtering. Before UFW and Firewalld, iptables was the primary choice for managing firewall rules—and it’s still widely used today.
📌 In this guide, we cover:
✅ What is iptables and how it evolved over time
✅ Differences between iptables, UFW, and Firewalld
✅ Best practices for securing your network
✅ A ready-to-use iptables configuration script
💡 Whether you’re new to Linux security or need a refresher, this guide will help you build a solid firewall strategy.
Introduction
When it comes to securing a Linux server, iptables is one of the most powerful tools available. It provides fine-grained control over network traffic, allowing administrators to define rules that permit or block connections based on various parameters. Whether you’re securing a personal server or managing a complex network, understanding iptables is essential.
Before UFW and Firewalld existed, iptables was the primary tool for managing firewall rules on Linux systems. It has been a fundamental component of Linux security since the early 2000s, giving system administrators direct control over packet filtering and network security policies. While modern tools like UFW and Firewalld offer simplified interfaces, they ultimately rely on iptables (or its successor, nftables) under the hood for enforcing firewall rules.
Origin of iptables
iptables originated as a replacement for ipchains, which was used in older Linux kernel versions. Introduced in Linux kernel 2.4, iptables brought a more modular and flexible approach to firewall management. Over the years, it has remained a fundamental component of Linux networking, although newer alternatives like nftables are now gaining traction.
Historical Timeline of Linux Firewall Tools
1998 - ipchains introduced as a replacement for ipfwadm (Linux 2.2)
2000 - iptables introduced in Linux kernel 2.4, replacing ipchains
2008 - UFW (Uncomplicated Firewall) introduced as a frontend for iptables (Ubuntu)
2011 - Firewalld introduced as a dynamic firewall management tool (RHEL/Fedora)
2014 - nftables introduced in Linux kernel 3.13 as a successor to iptablesThis progression highlights how Linux firewall tools have evolved, with iptables serving as a crucial foundation before newer tools simplified firewall management.
How iptables Works
iptables operates based on a system of tables and chains:
- 🔢 Tables define the types of rules (e.g.,
filter,nat,mangle). - 🌐 Chains determine how packets are processed (
INPUT,OUTPUT,FORWARD). - 🛠️ Rules specify conditions under which packets should be accepted, dropped, or modified.
By organizing rules within these structures, iptables enables precise traffic filtering and manipulation.
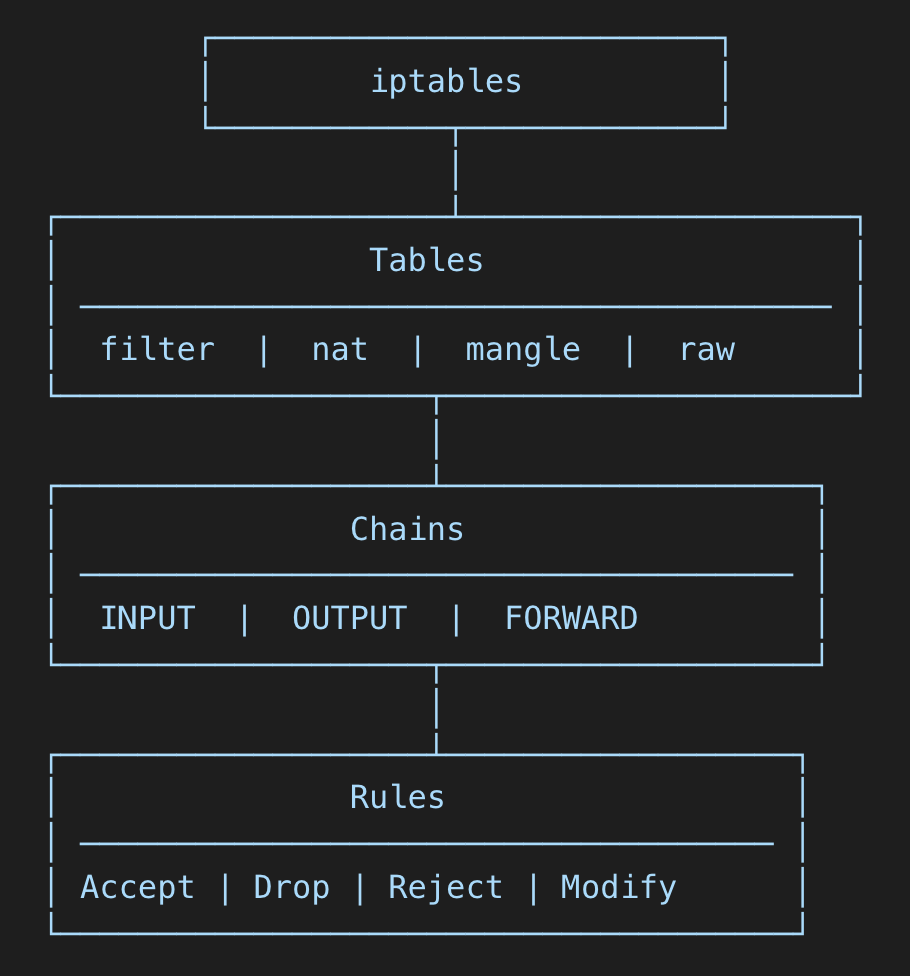
📌 Breakdown:
- Tables categorize rules based on function (
filter,nat,mangle, etc.). - Chains decide how packets are processed (
INPUT,OUTPUT,FORWARD). - Rules define what happens to a packet (allow, block, modify).
This structured approach makes iptables a powerful and flexible firewall solution! 🚀
Variants of iptables
While iptables is the most well-known, several variants and related tools exist:
- 🤖 nftables – A modern replacement for iptables, designed to be more efficient and easier to use.
- 🛡️ ebtables – Used for managing firewall rules on bridged networks.
- 🛡️ ip6tables – The IPv6 counterpart of iptables, ensuring firewall support for next-gen networking.
Since Linux kernel 3.13, nftables has been promoted as the successor to iptables due to its streamlined rule management and improved performance.
Comparison: iptables, ufw, and firewalld
| Feature | iptables | ufw | firewalld |
|---|---|---|---|
| Brief Information | Traditional Linux firewall tool directly interfacing with the netfilter kernel subsystem | Uncomplicated Firewall, a simplified interface for iptables | Dynamic firewall manager, default in RHEL/CentOS/Fedora |
| Release Date | 2000 | 2008 | 2011 |
| Primary Distros | All Linux distributions (legacy default) | Ubuntu, Debian-based distros | RHEL, CentOS, Fedora |
| Syntax Complexity | High – Complex syntax with chains, rules, and targets | Low – Simplified command structure | Medium – Zone-based approach with services |
| Configuration | Manual editing of complex rule sets | Simple command-line rules or basic config files | XML files and D-Bus interface |
| Dynamic Changes | Requires rule reloading | Supports dynamic changes | Fully dynamic without disrupting connections |
| Zone Support | No built-in zone concept | No built-in zone concept | Rich zone-based management |
| Default Config File | /etc/sysconfig/iptables | /etc/ufw/*.rules | /etc/firewalld/ |
| Rule Persistence | Requires extra steps for persistence | Persistent by default | Persistent by default |
| Connection Tracking | Basic | Basic (inherited from iptables) | Advanced |
| Runtime Changes | Changes apply immediately but aren’t persistent without saving | Changes are persistent by default | Changes can be runtime-only or permanent |
| IPv6 Support | Separate ruleset (ip6tables) | Integrated | Integrated |
| GUI Tools | Third-party only | Basic GUI (gufw) | firewall-config |
| Service Definitions | Not built in | Basic predefined apps | Extensive service definitions |
| Learning Curve | Steep | Gentle | Moderate |
| Direct iptables Support | Native | Underlying mechanism | Available via direct interface |
For those who prefer a user-friendly experience, ufw (Uncomplicated Firewall) is ideal for Debian/Ubuntu users, while firewalld is often used in Fedora and RHEL-based distributions.
iptables Configuration Examples
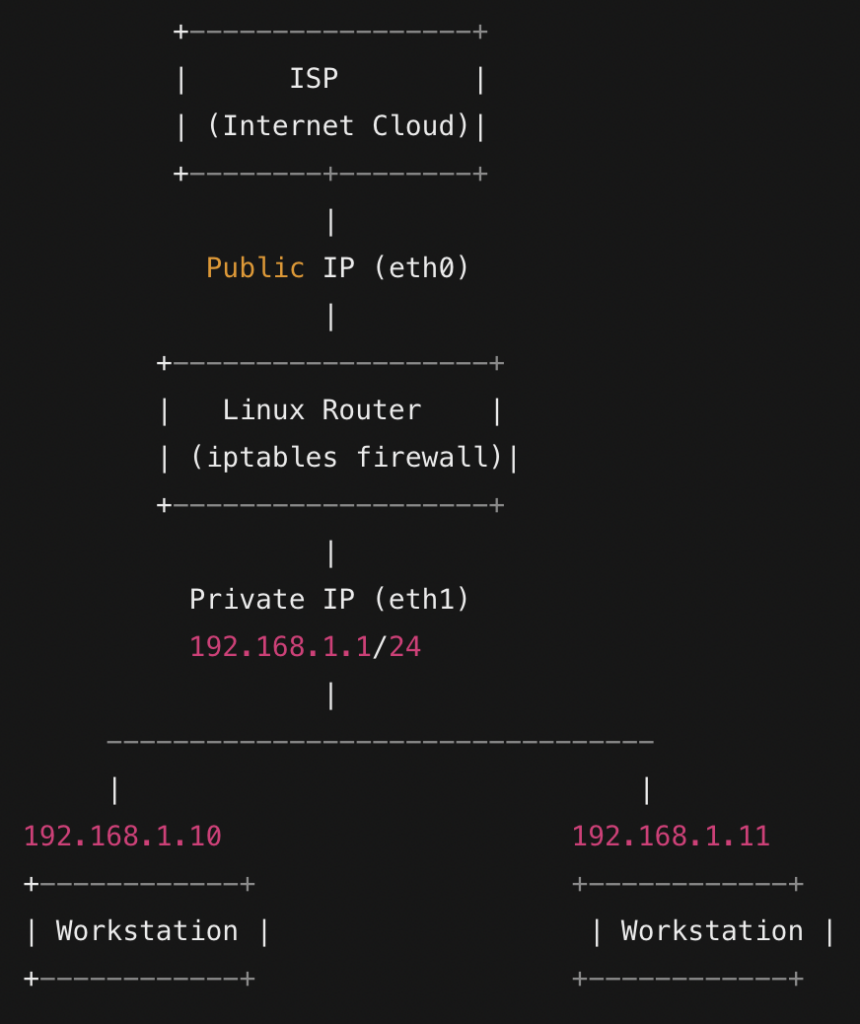
This diagram represents:
- A Linux router connected to the ISP using
eth0with a public IP. - An internal network (LAN) connected via
eth1, using the 192.168.1.0/24 subnet. - Two workstations within the LAN.
To help users manage their firewall rules efficiently, here’s a script that automates common iptables configurations. Save this as iptables_rules.sh, make it executable, and add it to /etc/rc.local for persistence.
Sample iptables Configuration Script
#!/bin/bash # iptables Essentials: A Beginner's Guide to Network Security # Source: Sandbox99.cc # Flush existing rules iptables -F iptables -X iptables -t nat -F iptables -t nat -X iptables -t mangle -F iptables -t mangle -X # Set default policies (Best practice: Drop all by default) iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT ACCEPT # Enable packet forwarding sysctl -w net.ipv4.ip_forward=1 # Allow localhost traffic iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT # Allow SSH, HTTP, and HTTPS traffic from LAN side (eth1) iptables -A INPUT -i eth1 -p tcp --dport 22 -j ACCEPT iptables -A INPUT -i eth1 -p tcp --dport 80 -j ACCEPT iptables -A INPUT -i eth1 -p tcp --dport 443 -j ACCEPT # Allow established and related connections iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT # Save rules iptables-save > /etc/iptables.rules
Applying the Script Automatically on Startup
- Save the script to
/usr/local/bin/iptables_rules.sh. - Make it executable:
chmod +x /usr/local/bin/iptables_rules.sh - Add it to
/etc/rc.localbeforeexit 0to ensure it runs at startup:/usr/local/bin/iptables_rules.sh - Reboot to apply changes:
reboot
This method ensures firewall rules are automatically applied after every reboot.
Best Practices for Configuring iptables
To maximize security and efficiency, consider the following best practices:
- ⛔ Default Deny Policy: Always block all traffic by default and allow only necessary connections.
- 🔍 Use Logging Sparingly: Enable logging for debugging but avoid excessive logging that can impact performance.
- 📃 Persist Rules: iptables rules do not survive reboots unless explicitly saved (
iptables-saveandiptables-restore). - 🌟 Minimize Rule Processing: Place frequently used rules at the top to improve performance.
- 🧠 Test Before Applying: Always test firewall rules in a controlled environment before deploying them in production.
Final Thoughts
iptables remains a cornerstone of Linux firewall management, providing powerful packet filtering capabilities. While nftables is gradually replacing it, many systems still rely on iptables for security and traffic control. Understanding its fundamentals will empower you to manage and secure your network effectively.




