Introduction
In the world of system administration, networking, and cybersecurity, efficiency and precision are not just goals—they’re necessities. The command line is your most powerful ally, and mastering it can turn complex, manual tasks into simple, automated commands. This guide will shine a light on three essential commands: echo, sed, and cat. We’ll explore how these tools work together to streamline file editing and manipulation. Whether you’re a system admin configuring a server, a network professional securing a system, or a cybersecurity expert performing an assessment, a strong grasp of these commands will empower you to manage configurations with speed and confidence.
Why You Need to Know This
In some critical situations, you’ll find yourself on a minimal system, like a stripped-down Docker container or a compromised machine, where familiar command-line editors such as nano, vi, or vim are not available. This is a common scenario for system administrators, cybersecurity professionals, and developers working with minimal environments. In these instances, you’re left with a core set of shell utilities. Knowing how to use echo, cat, and sed becomes essential for basic file operations.
These commands allow you to:
- Create or append to scripts: You can create a new script or add a function to an existing one without an editor.
- Modify configuration files: You can change a setting or append new lines to a configuration file to enable a service or change a parameter.
- Automate tasks: You can build simple shell scripts to perform these actions automatically, which is vital for system hardening, incident response, or deploying a quick fix.
Mastering these commands ensures that you can still perform fundamental system modifications and scripting even when your preferred tools are absent. This skill is a hallmark of an expert who can adapt and work effectively in any environment.
The cat command
# Example 1: Create or Overwrite a file cat > hello.txt <<EOF Hello World! How are you? EOF
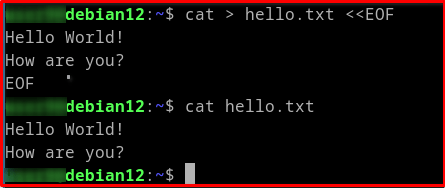
The > operator in example 1 will overwrite the file if it already exists, or create a new one.
# Example 2: Append the file cat >> hello.txt <<EOF New message here New config lines here EOF
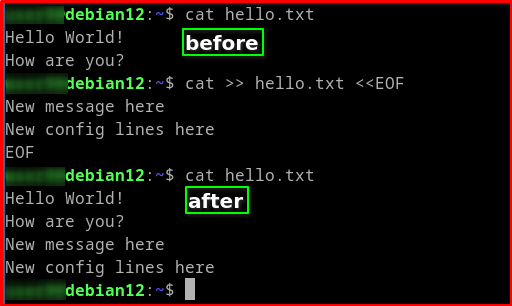
>>: This is the redirection operator in example 2 that appends the output
The echo command
# Example 1: Create or Overwrite a file echo 'first line Hello echo! How are you?' > hello.txt
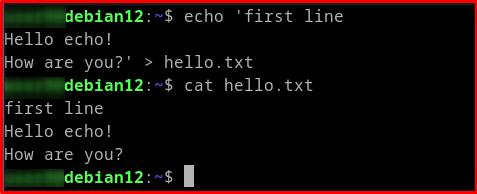
echo: This command prints the text that follows it.
The > operator in example 1 will overwrite the file if it already exists, or create a new one.'...': The single quotes ensure that the entire block of text is treated as a single string, including the newlines.hello.txt is your target file to create or modified if existing
# Example 2: Appends a file echo 'new line here this will appends a new line at the bottom' > hello.txt
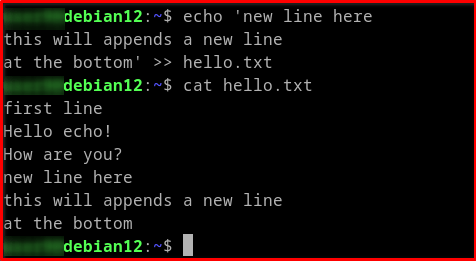
The >>: This is the redirection operator in example 2 that appends the output of the echo command to the specified file.
The sed command
# Config file config eth0 = '192.168.1.0/24' config eth1 = '192.168.100.1/24' config eth2 = '192.168.200.1/24' # End of line sed -i "s/^config eth2 = '.*'/config eth2 = '10.10.0.0\/24'/" test.conf
Command Breakdown
sed -i: This tellssedto edit the file in-place rather than just printing the modified content to the terminal.s/old_pattern/new_text/: This is the substitution command.sstands for substitute.^config eth2 = '.*': This is the pattern thatsedwill search for.^: Matches the beginning of a line.config eth2 = '.*': Matches the literal stringconfig eth2 = 'followed by any characters (.) until the end of the line ($). The single quotes in thesedcommand are important to ensure special characters are treated literally.
config eth2 = '10.10.0.0\/24': This is the new line that will replace the matched pattern. Notice that the forward slash in/24is escaped with a backslash (\) because the forward slash is the default delimiter for thescommand.
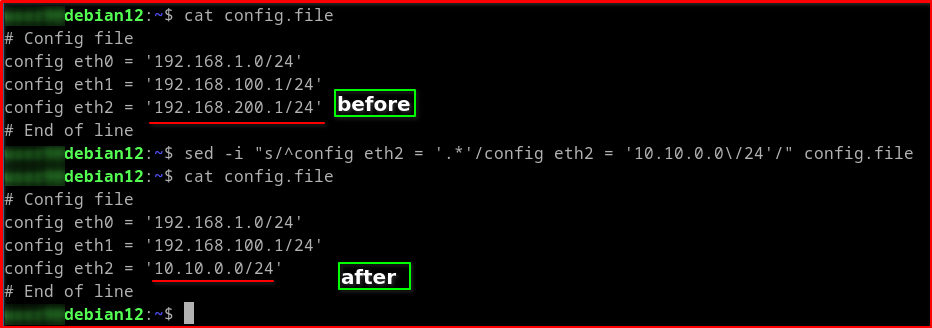
Note: I’m just showing you how this command can manipulate config files on Linux servers—you can use it to change whatever values you need.
Final Thoughts
The commands we’ve explored—echo for simple text output, sed for powerful in-place editing, and cat for multi-line file manipulation—are the cornerstones of effective shell scripting. For system and network administrators, this means effortlessly automating repetitive tasks like updating configuration files or adding new lines to scripts. For cybersecurity professionals, this knowledge is invaluable for both defense and offense. Blue teams can use these tools to quickly harden systems, modify log file parameters, or automate incident response tasks. Red teams can leverage them for creating payloads or swiftly modifying system files during a post-exploitation phase. By integrating echo, sed, and cat into your workflow, you’re not just saving time; you’re building a more robust and efficient foundation for all your operations.