Introduction
In the ever-evolving landscape of cybersecurity, hands-on experience is paramount. While theoretical knowledge forms the foundation, it’s the practical application of techniques that truly sharpens a security professional’s skills. As many of you know from my previous discussions on setting up bWAPP and Mutillidae II in Docker on Kali Linux, having a safe and controlled environment to practice is crucial. There’s nothing wrong with having more than one target machine in your Kali setup; in fact, it’s a huge advantage! You have the flexibility to switch between and explore different vulnerable applications, and the more targets you have, the better you can enhance your penetration testing skills. This is where tools like the Damn Vulnerable Web Application (DVWA) come into play. DVWA is an intentionally vulnerable web application, designed to provide a legal and safe environment for individuals to practice and hone their web penetration testing abilities.
This blog post will guide you through the essential aspects of DVWA, from understanding its purpose to setting it up efficiently within your Kali Linux environment using Docker. We’ll explore why DVWA is an indispensable resource for aspiring ethical hackers and seasoned security practitioners alike, and how leveraging its deliberate flaws can significantly enhance your understanding of common web vulnerabilities. Building upon our previous explorations of bWAPP and Mutillidae II, DVWA offers a distinct set of challenges and learning opportunities. By the end, you’ll have a clear grasp of how to utilize DVWA as a powerful training ground, enabling you to confidently identify, exploit, and ultimately mitigate real-world web application security risks.
Installing DVWA in Kali Linux via Docker
This section will guide you through the straightforward process of setting up DVWA on your Kali Linux environment using Docker. Leveraging Docker simplifies the installation, ensuring you have a consistent and isolated environment for your web security training. Feel free to visit the official docker hub where DVWA is hosted
Prerequisites:
Before you begin, ensure you have the following installed on your Kali Linux system:
If you don’t have Docker, Docker Compose and Git installed, you can follow the official Docker documentation for Kali Linux or use the following commands:
sudo apt update
sudo apt install docker.io docker-compose git
sudo systemctl start docker
sudo systemctl enable docker
# Add yourself to docker group
sudo usermod -aG docker ${USER}
# Logout or reboot your Kali machine after you add to docker group
Installation Steps:
Follow these steps to get DVWA up and running:
Step 1: Clone the DVWA Docker Repository: First, you’ll need to clone the specific GitHub repository that contains the Docker configuration for DVWA. Open your terminal in Kali Linux and execute:
git clone https://github.com/cytopia/docker-dvwa dvwa-docker cd dvwa-docker # Default credentials are not working with PHP 8.1 builds. # They function correctly with PHP 5.6 and 7.0 builds. # Let's edit the environment config file nano .env # Uncomment either version PHP-5.6 or PHP-7.0 save the file on exit. # Start the docker build make start
Note: This process might take a few minutes the first time as Docker downloads the required images. If you run docker-compose this is how would look like below.
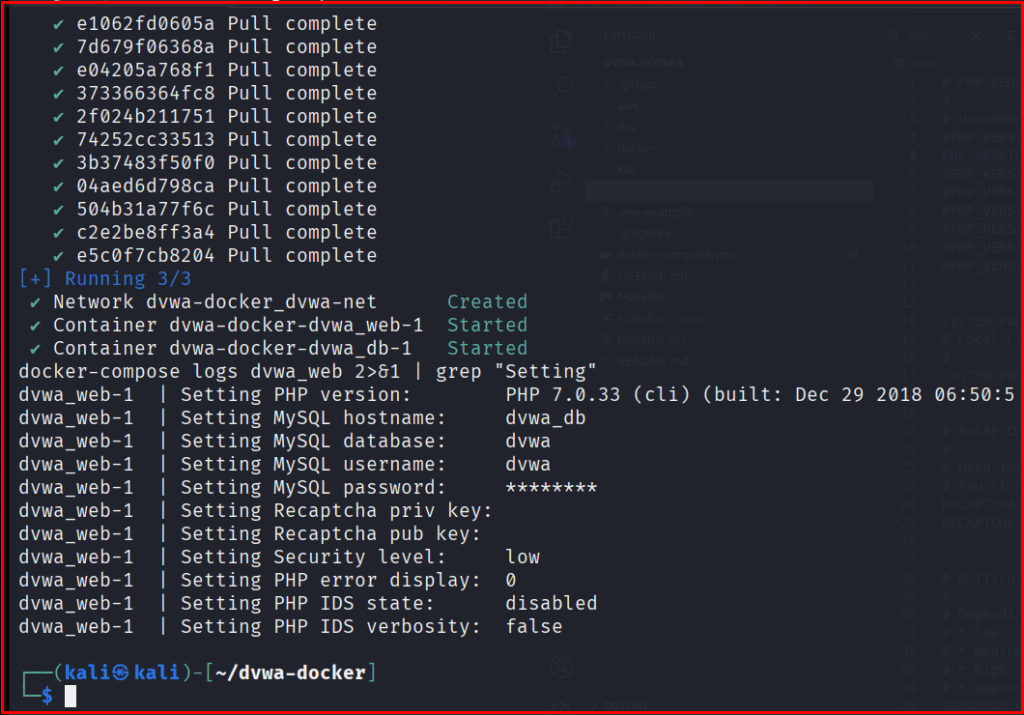
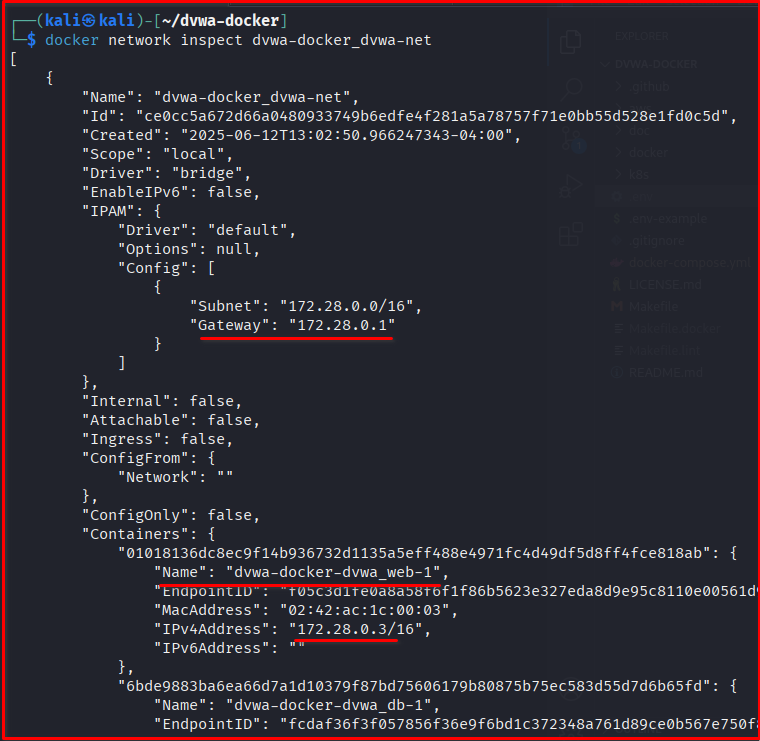
Step 2: Look for the IP Address of your container
docker network inspect dvwa-docker_dvwa-net
It’s important to note your IP address from the Docker network command (mine is 172.28.0.3). This IP is crucial for setting up your listener, as it will be your Kali Machine’s gateway IP address.
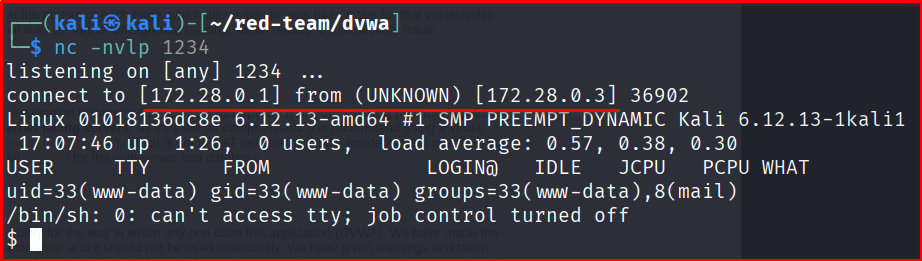
Step 3: To access DVWA, open your web browser and navigate to the IP address of your dvwa-docker-dvwa_web-1 container (for example, mine is http://172.28.0.3/login.php). Log in using the default credentials: admin:password. If you’re using localhost, remember to include port 8000 in the URL (e.g., http://localhost:8000/login.php).

Below is the sample screenshot when I upload and run /usr/share/webshell/php/php-reverse-shell.php file using docker gateway IP Address.
Final Thoughts: Takeaways and Insights
Bringing DVWA into your Kali Linux environment using Docker is more than just another installation; it’s a significant step in bolstering your web application security prowess. Here are the key takeaways and insights from this process:
Key Takeaways:
- Simplified Deployment with Docker: As demonstrated, Docker dramatically simplifies the setup of complex web applications like DVWA. Gone are the days of wrestling with intricate dependency issues, database configurations, and web server setups. With Docker, you can spin up a fully functional, vulnerable environment with just a few commands, allowing you to focus immediately on the learning and penetration testing aspects.
- A Safe and Legal Sandbox: DVWA provides a crucial sandbox for ethical hacking. It’s intentionally designed to be vulnerable, offering a safe and legal space to experiment with various attack vectors without the risk of harming real-world systems or facing legal repercussions. This controlled environment is invaluable for developing and refining your skills.
- Diverse Vulnerability Exposure: DVWA covers a wide array of common web vulnerabilities, including SQL Injection, Cross-Site Scripting (XSS), Command Injection, File Inclusion, and more. Each vulnerability typically comes with different security levels (low, medium, high, impossible), allowing you to gradually increase the challenge and understand how various coding practices affect security.
Practical Insights:
- The Power of a Multi-Target Lab: Building on our previous discussions about bWAPP and Mutillidae II, incorporating DVWA truly highlights the benefit of maintaining a multi-target lab within your Kali Linux setup. Each vulnerable application offers unique scenarios and nuances in how vulnerabilities manifest and are exploited. Having a diverse set of targets allows you to:
- Broaden your understanding: Exposing yourself to different applications developed with varying frameworks and coding styles helps you identify vulnerabilities across diverse environments.
- Adapt your techniques: What works on one application might not work on another. Multiple targets force you to adapt your reconnaissance, exploitation, and post-exploitation techniques, making you a more versatile penetration tester.
- Continuous Skill Enhancement: The more “breakable” applications you have at your fingertips, the more opportunities you create for continuous learning and skill refinement. This proactive approach to practice is vital in the fast-paced world of cybersecurity.
- Bridging Theory and Practice: DVWA serves as an excellent bridge between theoretical knowledge of web vulnerabilities and their practical exploitation. Reading about SQL injection is one thing; successfully exploiting it on DVWA and understanding its impact firsthand is another. This hands-on experience solidifies concepts and builds muscle memory for identifying and mitigating real-world weaknesses.
- Foundation for Advanced Learning: Mastering the vulnerabilities within DVWA provides a solid foundation for tackling more complex challenges. The techniques you learn here are transferable and applicable to understanding and exploiting vulnerabilities in more sophisticated applications, preparing you for real-world penetration testing engagements and certifications.
In essence, setting up DVWA with Docker on Kali Linux isn’t just about getting another tool running; it’s about strategically building a robust, versatile, and accessible learning environment. Embrace the vulnerabilities, break things responsibly, and watch your web security skills soar.