Understanding Reflected Cross-Site Scripting (XSS)
Reflected XSS is a common web security vulnerability that occurs when a web application takes user-supplied input and immediately returns it in an unvalidated or unfiltered form, leading to the execution of malicious scripts in the user’s browser. Unlike Stored XSS (where the malicious script is permanently saved on the server), Reflected XSS payloads are delivered via a single request and are not persistent. They are “reflected” off the web server, typically in an error message, search result, or any other response that includes some or all of the input sent by the user.
The attacker’s goal is to trick a victim into clicking a specially crafted URL containing the malicious script. When the victim clicks this link, their browser makes a request to the vulnerable web application. The application then reflects the malicious script back to the victim’s browser, which, believing the script originates from a trusted domain, executes it.
What can an attacker do with Reflected XSS?
Once a Reflected XSS vulnerability is successfully exploited, an attacker can:
- Steal Session Cookies: This allows the attacker to hijack the victim’s session and impersonate them, gaining access to their account without needing credentials.
- Deface the Website (client-side): While not persistent, the attacker can alter the appearance of the website for the victim.
- Redirect Users: Phish victims by redirecting them to malicious websites.
- Perform Malicious Actions: Execute arbitrary JavaScript, make AJAX requests, or interact with other parts of the web application on behalf of the victim.
- Keylogging: Capture keystrokes entered by the victim on the compromised page.
Diagram Flow: How Reflected XSS Works
Let’s illustrate the typical flow of a Reflected XSS attack.
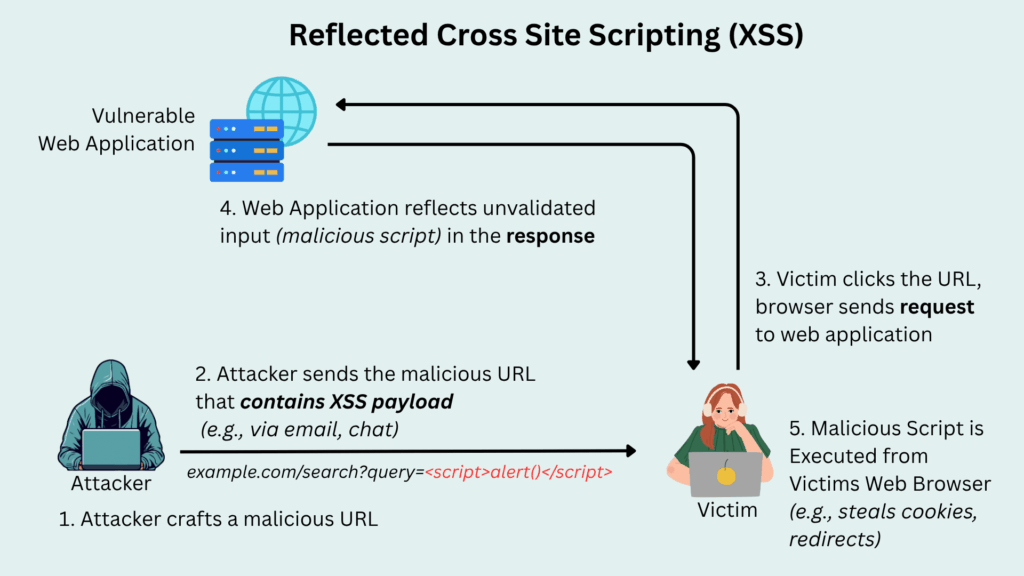
Detailed Steps:
- Attacker Crafts Malicious URL: The attacker identifies a vulnerable parameter in a web application (e.g., a search field, an error message handler) that doesn’t properly sanitize user input. They then craft a URL that includes a malicious script within this vulnerable parameter. For example:
https://example.com/search?query=<script>alert('XSSed!')</script> - Attacker Delivers Malicious URL: The attacker sends this crafted URL to the victim. This can be done through various social engineering techniques, such as an email, a chat message, or a link on a seemingly legitimate website.
- Victim Clicks the URL: The victim, unaware of the malicious nature of the URL, clicks on it. Their web browser then sends an HTTP GET request to the vulnerable web application, including the malicious script as part of the
queryparameter. - Vulnerable Web Application Reflects Input: The web application receives the request. Instead of sanitizing or encoding the
queryparameter before displaying it, it directly embeds the malicious script into the HTML response. For example, the server might return:<html><body>Your search for <script>alert('XSSed!')</script> yielded no results.</body></html> - Malicious Script Execution: The victim’s web browser receives the HTML response. When parsing the HTML, it encounters the
<script>tag. Because the script appears to originate from the trustedexample.comdomain, the browser executes the JavaScript code within the script tag. In this example, an alert box displaying “XSSed!” would pop up on the victim’s screen. In a real attack, this script would likely perform more damaging actions, such as stealing cookies or redirecting the user.
Real-World Use: Detection and Remediation
Reflected XSS is a persistent threat in the real world, and understanding how to detect and remediate it is crucial for web security.
How to Detect Reflected XSS Vulnerabilities
Detection often involves a combination of automated and manual techniques:
- Manual Inspection (Code Review):
- Input Points: Identify all user-controlled input points in the application (URL parameters, form fields, HTTP headers like
Referer,User-Agent,Cookie). - Output Points: Trace where these inputs are reflected back into the HTML response.
- Lack of Sanitization/Encoding: Look for instances where input is directly embedded into the HTML without proper output encoding (e.g., using
echo $_GET['param']in PHP withouthtmlspecialchars()). - Contextual Analysis: Understand the context in which the input is reflected. Different contexts (HTML attributes, JavaScript code, CSS) require different encoding schemes.
- Input Points: Identify all user-controlled input points in the application (URL parameters, form fields, HTTP headers like
- Automated Scanners (DAST – Dynamic Application Security Testing):
- Web Vulnerability Scanners: Tools like OWASP ZAP, Burp Suite Professional, Nessus, Acunetix, and QualysGuard Web Application Scanning can automatically crawl web applications, inject XSS payloads into various parameters, and analyze the responses for evidence of script execution.
- Payload Injection: These scanners inject a wide range of XSS payloads (e.g.,
<script>alert(1)</script>,"><img src=x onerror=alert(1)>,javascript:alert(1)) into all detected input fields and parameters. - Response Analysis: They monitor the browser’s behavior (e.g., pop-up alerts, changes in DOM) or analyze the HTTP responses for reflected payloads without proper encoding.
- Manual Testing (Penetration Testing):
- Browser-Based Testing: Manually input XSS payloads into forms, URL parameters, and other input fields. Observe if the script executes in the browser.
- Burp Suite Repeater/Intruder: Use tools like Burp Suite’s Repeater to modify requests and test different payloads. Intruder can be used for automated brute-forcing of payloads.
- Content Security Policy (CSP) Assessment: While not a direct detection method for the vulnerability itself, analyzing an application’s CSP can reveal if it has protection mechanisms in place that would mitigate XSS. A weak or absent CSP can be an indicator of potential XSS risk.
How to Remediate Reflected XSS Vulnerabilities
Remediation primarily focuses on input validation and, more importantly, output encoding.
- Output Encoding (Most Critical):
- Contextual Encoding: This is the most effective defense. Before reflecting any user-supplied data back into the HTML, it must be properly encoded based on the context in which it’s being placed.
- HTML Entity Encoding: For data placed within HTML body or attributes (e.g.,
<input value="USER_INPUT">), convert characters like<,>,",',&into their HTML entities (<,>,",',&).- Example (PHP):
echo htmlspecialchars($_GET['query'], ENT_QUOTES, 'UTF-8'); - Example (JavaScript for HTML):
element.textContent = user_input;orelement.setAttribute('value', user_input);(avoidinnerHTMLwith untrusted input).
- Example (PHP):
- JavaScript Encoding: For data placed within JavaScript code (e.g.,
<script>var name = "USER_INPUT";</script>), escape characters like\,",',/, and control characters.- Example:
JSON.stringify(user_input)for embedding into JavaScript data structures.
- Example:
- URL Encoding: For data placed within URL parameters.
- Example (PHP):
echo urlencode($_GET['param']);
- Example (PHP):
- HTML Entity Encoding: For data placed within HTML body or attributes (e.g.,
- Use Secure Templating Engines: Many modern web frameworks and templating engines (e.g., React, Angular, Jinja2, Twig) have built-in auto-escaping mechanisms that, when configured correctly, automatically perform output encoding. Ensure these features are enabled and not bypassed.
- Contextual Encoding: This is the most effective defense. Before reflecting any user-supplied data back into the HTML, it must be properly encoded based on the context in which it’s being placed.
- Input Validation and Sanitization (Secondary but Important):
- Whitelisting: Define strict rules for what constitutes valid input. For example, if a field should only contain numbers, reject any input that contains letters or symbols.
- Blacklisting (Use with Caution): While less effective than whitelisting, blacklisting attempts to filter out known malicious characters or patterns. This is prone to bypasses due to the constantly evolving nature of XSS payloads. Avoid relying solely on blacklisting.
- Length and Type Checks: Enforce limits on input length and ensure data types are correct.
- Content Security Policy (CSP):
- Defense in Depth: Implement a strong Content Security Policy (CSP) header. CSP allows you to whitelist trusted sources of content (scripts, stylesheets, etc.) that the browser is allowed to load and execute. Even if an XSS vulnerability exists, a well-configured CSP can prevent the injected script from executing or making external requests.
- ‘unsafe-inline’ and ‘eval’: Avoid
unsafe-inlinefor scripts andeval()functions in your CSP, as these can significantly weaken its protection against XSS.
- HTTP-Only Cookies:
- Set the
HttpOnlyflag on session cookies. This prevents client-side JavaScript (including malicious XSS scripts) from accessing the cookie, thereby mitigating session hijacking.
- Set the
- Security Headers:
- X-XSS-Protection: While largely deprecated in modern browsers (replaced by CSP), this header used to provide some basic XSS filtering. It’s generally better to rely on CSP.
- X-Content-Type-Options: nosniff: Prevents browsers from MIME-sniffing a response away from the declared content type.
- Regular Security Audits and Penetration Testing:
- Regularly scan your applications for vulnerabilities and conduct professional penetration tests to identify and address XSS flaws before they can be exploited.
Final Thoughts
Reflected XSS is a subtle yet powerful vulnerability that remains a significant threat to web applications. Here are the key takeaways and lessons learned:
- Trust No Input: The fundamental principle of web security is to never trust user-supplied input. Every piece of data coming from the client must be treated as potentially malicious.
- Output Encoding is King: While input validation is important, output encoding is the primary and most effective defense against XSS. It prevents the browser from interpreting user data as executable code. Always encode data at the point where it is output to the browser, based on the specific HTML context.
- Context Matters: There is no one-size-fits-all encoding. The type of encoding required depends entirely on where the user-supplied data is being placed in the HTML document (e.g., inside an HTML tag, an HTML attribute, a JavaScript block, a URL).
- Defense in Depth: Relying on a single defense mechanism is risky. Implement multiple layers of security, including proper output encoding, input validation, a robust Content Security Policy, and HttpOnly cookies, to create a strong defense against XSS.
- Automated Tools vs. Manual Review: Automated scanners are excellent for identifying common XSS patterns, but they are not infallible. Manual code review and skilled penetration testing are crucial for uncovering more complex or context-specific XSS vulnerabilities.
- Stay Updated: The landscape of web vulnerabilities and attack techniques is constantly evolving. Keep your development team informed about the latest security best practices, patches for frameworks, and emerging XSS bypass techniques.
- Educate Developers: Security should be ingrained in the development lifecycle from the beginning. Educating developers about XSS and secure coding practices is paramount to building resilient applications.
- User Awareness: While not a technical remediation for the vulnerability itself, educating users about the dangers of clicking suspicious links can reduce the success rate of Reflected XSS attacks, as these often rely on social engineering.
By diligently applying these principles, organizations can significantly reduce their exposure to Reflected XSS attacks and better protect their users and data.