Introduction In the rapidly evolving world of AI-assisted development, prompt files are becoming the unsung heroes of consistency, reproducibility, and collaboration. Instead of typing lengthy instructions into an AI tool every time, prompt files let you store those...
Sandbox99 Chronicles
From My Sandbox to Yours — Practical IT Insights.
Dig Command Cheat Sheet – Mastering DNS Queries Like a Pro
Introduction When it comes to DNS troubleshooting and querying DNS records directly from the command line, the dig (Domain Information Groper) command is an essential tool for system administrators, network engineers, and penetration testers.This cheat sheet provides...
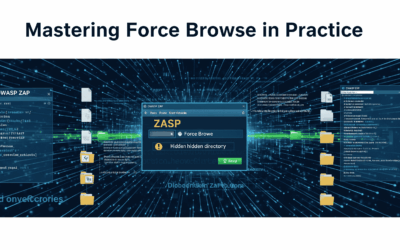
Mastering Force Browse in Practice
Introduction In the intricate world of web application security, "force Browse" stands as a fundamental technique for uncovering hidden vulnerabilities. It's the art of systematically guessing or predicting URLs, directories, and files that might not be directly...
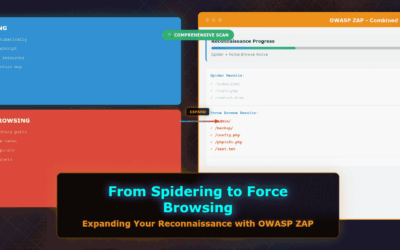
From Spidering to Force Browsing: Expanding Your Reconnaissance with OWASP ZAP
Introduction Web application security testing is a critical practice for identifying and mitigating vulnerabilities before they can be exploited. A fundamental step in this process is reconnaissance – gathering as much information as possible about the target...
Mastering Curl in Kali Linux: Your Go-To Tool for Network Interaction and Ethical Hacking Part 2
I. Advanced Curl Techniques for Ethical Hacking This is our previous blogs related to curl. Beyond basic reconnaissance, curl truly shines when you need to craft custom HTTP requests, simulate complex user interactions, or bypass certain security measures. This is...
Mastering Curl in Kali Linux: Your Go-To Tool for Network Interaction and Ethical Hacking Part 1
I. Introduction: The Power of Curl in Your Kali Arsenal In the vast and ever-evolving landscape of cybersecurity, a penetration tester's toolkit is their most valuable asset. While Kali Linux boasts an impressive array of specialized tools for every conceivable task,...