🔒 UFW for Beginners: Firewall Security Without the Complexity
Tired of complex firewall configurations? In my latest blog post, I break down UFW – the perfect firewall solution for Linux systems that provides robust security without the complexity.
What you’ll learn:
- 🚀 How UFW simplifies firewall management compared to direct iptables
- 🛠️ Step-by-step installation and configuration on various Linux distributions
- 🔧 Sample configurations for common scenarios (web servers, home networks)
- 🛡️ Best practices for securing your systems effectively
Whether you’re a Linux beginner or seasoned sysadmin, this comprehensive guide will help you implement proper network security with minimal effort.
Introduction to UFW
Uncomplicated Firewall (UFW) is a frontend for iptables/nftables designed to simplify the process of configuring a firewall on Linux systems. Developed by Ubuntu in 2008, UFW was created to address the complexity of directly managing iptables, which often presented a steep learning curve for system administrators and hobbyists alike.
The philosophy behind UFW is in its name – “Uncomplicated.” While iptables offers tremendous power and flexibility, UFW provides a more accessible interface without sacrificing essential functionality. It abstracts away many of the complex details while still leveraging the robust filtering capabilities of the underlying netfilter framework.
UFW serves as an intermediate layer between the user and iptables/nftables (depending on your system’s version), translating simple commands into the appropriate iptables/nftables rules. This relationship means that while UFW makes configuration easier, it still benefits from the performance and security of the battle-tested netfilter infrastructure.
Why Use UFW?
Benefits over direct iptables configuration
- 🔄 Simplified syntax: UFW commands are intuitive and concise
- 📉 Reduced learning curve: New administrators can quickly implement effective firewall rules
- 🔄 Consistent interface: Works similarly across different Linux distributions
- 🛡️ Safer defaults: Helps prevent accidental misconfigurations
- 📦 Application profiles: Pre-configured rule sets for common services
Use cases
- 💻 Personal Linux workstations
- 🖥️ Small to medium-sized servers
- 🏠 Home lab environments
- 🎓 Educational purposes to learn firewall concepts
- ⏱️ Quick deployment scenarios where time is limited
Limitations
- 🔍 Less granular control compared to direct iptables management
- 🧩 Fewer advanced features (though many can still be implemented)
- 🏢 Not ideal for complex enterprise environments with specific requirements
- 🔒 May not expose all features of underlying iptables/nftables capabilities
Installation and Basic Setup
Installation
On Debian/Ubuntu-based systems:
sudo apt update sudo apt install ufw
On Fedora/RHEL-based systems:
sudo dnf install ufw
On Arch Linux:
sudo pacman -S ufw
Initial Configuration
First, check the status of UFW:
sudo ufw status
Before enabling UFW, ensure you won’t lock yourself out by allowing SSH access:
sudo ufw allow ssh
Set default policies (deny incoming, allow outgoing):
sudo ufw default deny incoming sudo ufw default allow outgoing
Enable the firewall:
sudo ufw enable
Verify the configuration:
sudo ufw status verbose
Understanding UFW Concepts
Default Policies
UFW operates on the concept of default policies that define the baseline behavior for traffic:
- 🚫 Incoming traffic: Typically set to “deny” for security
- ✅ Outgoing traffic: Typically set to “allow” for convenience
- 🔄 Forwarded traffic: Controls packets moving through the system (important for routers)
These defaults act as fallbacks when no specific rule matches a connection.
Rules and Rule Ordering
UFW evaluates rules in the order they are added, with the first matching rule determining the fate of a packet. This is critical to understand, as a more specific rule placed after a broader rule might never be reached.
Rules can be based on:
- 🌐 Source/destination IP addresses
- 🔌 Network interfaces
- 🔢 Ports and protocols
- 🔄 Direction (incoming/outgoing)
Profiles and Applications
UFW includes application profiles that simplify the process of allowing traffic for common services. These profiles are typically stored in /etc/ufw/applications.d/ and can be listed with:
sudo ufw app list
Profiles define the necessary ports and protocols for applications, making it easier to create appropriate firewall rules without memorizing port numbers.
Sample Configurations
Basic Server Setup
This configuration secures a typical web server:
# Allow SSH for remote administration sudo ufw allow ssh # Allow HTTP and HTTPS sudo ufw allow 80/tcp sudo ufw allow 443/tcp # Allow FTP if needed sudo ufw allow 21/tcp # Enable the firewall sudo ufw enable
Home Network Configuration
For a home server providing various services:
# Allow SSH, but restrict to local network sudo ufw allow from 192.168.1.0/24 to any port 22 # Allow media server access sudo ufw allow 32400/tcp # Plex Media Server sudo ufw allow 8096/tcp # Jellyfin/Emby # Allow network file sharing sudo ufw allow 139/tcp # Samba sudo ufw allow 445/tcp # Samba sudo ufw allow 2049/tcp # NFS # Enable the firewall sudo ufw enable
Network Diagram Visualization
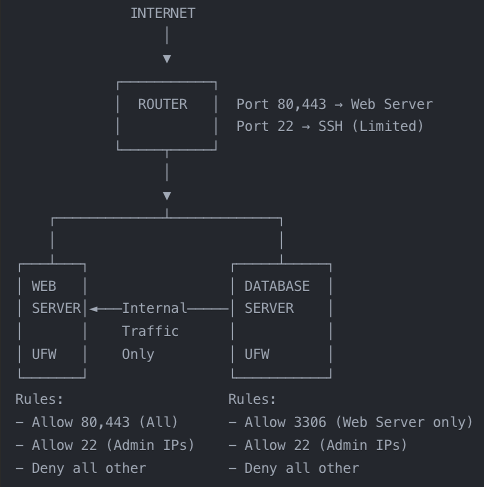
Common Rule Examples
# Allow specific IP address sudo ufw allow from 192.168.1.100 # Allow specific IP range to specific port sudo ufw allow from 192.168.1.0/24 to any port 22 # Allow specific port range sudo ufw allow 6000:6007/tcp # Deny specific traffic sudo ufw deny 25/tcp # Allow traffic on specific interface sudo ufw allow in on eth0 to any port 80 # Limit SSH connections (rate limiting) sudo ufw limit ssh
Best Practices
Security Recommendations
- 🔒 Default deny: Always start with a default deny policy for incoming traffic
- 🎯 Specific rules: Be as specific as possible with your rules (limit by source IP, interface, etc.)
- 🔑 Least privilege: Allow only what’s necessary, nothing more
- 🔍 Regular audits: Periodically review your rules with
sudo ufw status numbered - 💾 Backup configuration: Save your rules with
sudo ufw show raw > ufw-backup.rules
Performance Considerations
- ⚡ Keep rule sets minimal and efficient
- 🏎️ Place most frequently matched rules at the top of your ruleset
- 🖥️ Consider hardware resources when implementing extensive logging
- 📦 Use application profiles when possible instead of port-based rules
Maintenance and Updates
- 📊 Review firewall logs regularly for unexpected blocked traffic
- 🔄 Update rules when new services are deployed
- 🗑️ Remove rules for decommissioned services
- 🧪 Test rule changes in non-production environments first
Common Mistakes to Avoid
- 🚪 Enabling UFW before allowing SSH access (results in lockout)
- 🕳️ Creating overly permissive rules that undermine security
- 🔙 Forgetting to account for return traffic
- ⚠️ Not testing rules before implementing in production
- 🔄 Adding redundant or conflicting rules
Troubleshooting
Diagnosing Connection Issues
If services aren’t accessible after configuring UFW:
- Check UFW status:
sudo ufw status verbose - Test with UFW disabled temporarily:
sudo ufw disable- # Test connection
sudo ufw enable
- Check for blocking rules:
sudo ufw status numbered - Review UFW logs:
sudo grep UFW /var/log/syslog
Resolving Rule Conflicts
When rules appear to conflict:
- List rules in processing order:
sudo ufw status numbered - Delete problematic rules:
sudo ufw delete [rule number] - Add more specific rules before general ones
Recovery from Lockouts
If you’ve locked yourself out via SSH:
- Access the physical machine or console
- Disable UFW:
sudo ufw disable - Add proper SSH rule:
sudo ufw allow ssh - Re-enable UFW:
sudo ufw enable
Final Thoughts
UFW excels at what it was designed to do – provide a straightforward interface for managing firewall rules on Linux systems. It strikes an excellent balance between usability and security, making it perfect for individual users, small teams, and environments where simplicity is valued.
However, a firewall is just one component of a comprehensive security strategy. UFW should be complemented with other security measures like:
- 🔄 Regular system updates
- 🔐 Strong authentication mechanisms
- 🚨 Intrusion detection systems
- 📊 Security monitoring and logging
- 👨🏫 User education and awareness
The future of UFW seems secure as it continues to be maintained and included in major distributions. As the underlying netfilter framework evolves (particularly with the transition from iptables to nftables), UFW will likely adapt to maintain its position as the friendly face of Linux firewalls.