Introduction
The fundamental purpose remains the same: gaining a shell. This means achieving remote command execution on a target system, giving us the ability to interact with it as if we were sitting right in front of it.
Just to quickly recap, a Reverse Shell is characterized by the victim machine initiating a connection back to the attacker. The attacker, in turn, is listening for this incoming connection. This method is incredibly effective when the target system is behind a firewall that restricts inbound connections but allows outgoing ones. It’s like calling out from a locked room – you can make the call, but no one can call you directly.
But what if the scenario is different? What if the target system can receive incoming connections, or you’re already operating within an internal network where such direct access is feasible? This is precisely where the Bind Shell shines. Unlike its “reverse” sibling, a bind shell involves the target system opening a listening port and waiting for you, the attacker, to connect to it. It’s a fundamental concept in networking, and in the context of security, it represents another avenue for remote access.
What is a Bind Shell?
At its core, a Bind Shell is a type of shell where the target machine (the victim) “binds” to a specific port, meaning it opens that port and starts listening for incoming connections. Once an attacker connects to this listening port, the shell is established, and the attacker gains the ability to execute commands on the victim machine.
Imagine the victim machine setting up a “door” on its network, labeling it with a specific “door number” (the port). It then patiently waits by this door. The attacker, knowing the victim’s address and the door number, simply walks up and knocks. Once the connection is established, communication flows freely.
How a Bind Shell Works
Let’s break down the technical steps involved in establishing a bind shell.
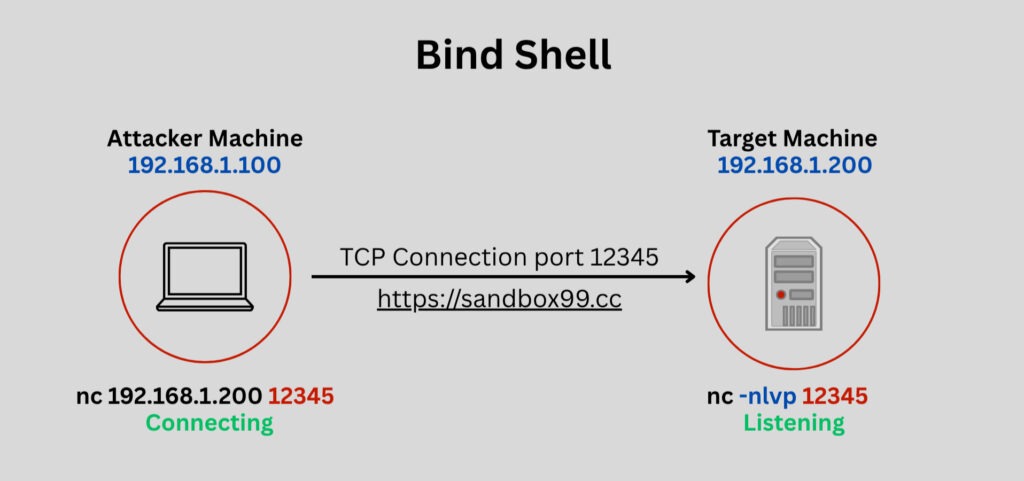
A. Setting Up the Listener (Target Side)
The critical first step is making the target machine listen for connections. This can be achieved through various means, depending on the operating system and the attacker’s capabilities.
- Netcat (
nc): Often called the “TCP/IP Swiss Army knife,”netcatis a classic tool for this purpose.- On a Linux system, a common command might look like:
nc -nlvp 12345 -e /bin/bash-n: Numeric-only IP addresses (avoids DNS lookups, faster).-l: Listen mode-v: Verbose output-p12345: Specify port 12345 to listen on-e /bin/bash: Execute/bin/bash(the shell) upon successful connection and redirect its input/output over the network.
- For Windows, it would be similar, but executing
cmd.exe:nc -nlvp 12345 -e cmd.exe
- On a Linux system, a common command might look like:
- Scripting Languages: Python, Perl, and PHP are frequently used to create simple bind shell listeners, especially when
netcatmight not be available or the attacker wants to avoid leaving obvious forensic traces. These scripts typically involve socket programming to create a listener and then spawn a shell process, redirecting I/O. - Dedicated Malware: In real-world scenarios, sophisticated malware often includes built-in bind shell capabilities, making it seamless for an attacker to establish control after initial compromise.
The choice of port (e.g., 12345) is important. While common ports like 80 (HTTP) or 443 (HTTPS) might be tempting for stealth, they are often already in use by legitimate services. High-numbered ports (above 1024) are frequently chosen to avoid conflicts, though they can also be more easily flagged as suspicious by network monitoring tools. Sometimes, attackers might try to “masquerade” by listening on a well-known port if the legitimate service is not running, hoping to blend in with normal traffic.
B. Connecting from the Attacker Side
Once the target machine is listening, the attacker simply needs to connect to it. Again, netcat is the go-to tool.
- From the attacker’s machine:
nc <target_ip_address> <target_port>For example, if the target’s IP is192.168.1.200and it’s listening on port 12345:nc 192.168.1.200 12345Upon executing this command,netcatattempts to establish a TCP connection to the specified IP and port. If successful, the attacker’s terminal is directly connected to the shell running on the victim machine.
C. Data Flow
Once the TCP connection is established, all subsequent commands typed by the attacker are sent over this connection to the shell process running on the victim. The output of these commands (e.g., directory listings, error messages) is then sent back over the same connection to the attacker’s terminal. This creates an interactive, albeit remote, command-line interface.
Limitations and Challenges of Bind Shells
Despite their utility in specific contexts, bind shells come with significant limitations that often make them less preferred than reverse shells in modern networks:
- Firewall Rules: This is the biggest hurdle. Most modern networks implement strict inbound firewall rules that block all unsolicited incoming connections by default. Unless a specific port is intentionally opened for legitimate services, a bind shell attempt will be denied.
- Network Address Translation (NAT): The vast majority of devices (laptops, desktops, internal servers) operate behind Network Address Translation (NAT). This means their private IP addresses are not directly reachable from the public internet. To connect to a bind shell on such a machine, port forwarding would need to be manually configured on the router/firewall, a task highly unlikely to be done by a legitimate user and difficult for an attacker to achieve without prior compromise of the network device itself.
- Detection: A machine listening on a non-standard port for a shell is relatively easy to detect through network scanning tools (like Nmap). Security teams frequently scan their own networks for unexpected open ports. Active bind shells also create a persistent listening service, which can be identified by network monitoring systems.
- Dynamic IP Addresses: If the target machine has a dynamic public IP address (which changes periodically), the attacker’s ability to connect to the bind shell is transient. Once the IP changes, the previous connection details become invalid.
Ethical Considerations and Prevention
Understanding bind shells, like any other hacking technique, is a double-edged sword. This knowledge is intended for defensive and ethical hacking purposes only. Using these techniques for unauthorized access to systems is illegal and carries severe consequences.
Defensive Measures to Mitigate Bind Shell Risks:
- Robust Firewall Configurations: Implement the principle of “deny all by default.” Only explicitly allow necessary inbound connections for legitimate services. Regularly review and audit firewall rules.
- Network Intrusion Detection/Prevention Systems (NIDS/NIPS): Deploy these systems to monitor network traffic for suspicious patterns, including attempts to establish bind shells or unusual listening ports. NIPS can actively block such attempts.
- Regular Vulnerability Scanning and Patching: Keep all operating systems, applications, and network devices patched and updated. Vulnerabilities are often the initial entry point for an attacker to gain code execution and establish a shell.
- Least Privilege Principle: Ensure users and applications operate with the absolute minimum necessary permissions. This limits the damage an attacker can do even if they manage to compromise a system.
- Network Segmentation: Divide your network into smaller, isolated segments. This limits an attacker’s ability to move laterally and establish bind shells on other systems once one machine is compromised.
Final Thoughts
In wrapping up our discussion on bind shells, we’ve seen how they differ fundamentally from reverse shells, primarily in who initiates the connection and their distinct advantages and disadvantages.
Key Takeaways:
- A Bind Shell involves the target system listening for an incoming connection from the attacker.
- It’s most effective when the target has a public IP address or when operating within a less-restricted internal network.
- Its primary challenges are modern firewall rules and Network Address Translation (NAT), which make direct inbound connections difficult.
Ultimately, neither bind shells nor reverse shells are inherently “better.” Their effectiveness hinges entirely on the specific network environment, the target’s security posture, and the attacker’s objectives. A skilled security professional or attacker will choose the appropriate shell type based on the context.
Continue your journey in cybersecurity by always seeking to understand both offensive and defensive methodologies. The more you comprehend attack vectors, the better equipped you’ll be to defend against them.
Further Reading & Resources
Looking for quick references or want to explore Netcat’s full capabilities? These cheatsheets are invaluable:
- Bind Shell Cheatsheet: [Link to Bind Shell Cheatsheet]