🔒 Understanding Proxy Servers: Security, Performance, and Best Practices 🚀
In today’s digital landscape, proxy servers play a crucial role in enhancing privacy, improving network performance, and securing enterprise environments. Whether you’re managing a corporate IT infrastructure or simply curious about how proxies work, understanding their advantages, challenges, and real-world applications is essential.
In my latest blog post, I dive into:
✅ What is a proxy server, and how does it work?
✅ Spotlight on Squid: The Pioneer of Proxy Servers
✅ Safety Concerns with Public Proxies
✅ Legal and Ethical Considerations
✅ Security Best Practices for Proxy Users
Introduction
In today’s interconnected digital world, proxy servers play a crucial role in how data moves across networks. Whether you’re concerned about privacy, looking to improve network performance, or managing access to online content, understanding proxy servers is essential for both individuals and organizations.
A proxy server acts as an intermediary between your device and the internet, routing your traffic through another server before it reaches its destination. This seemingly simple concept has profound implications for security, privacy, and network management.
This guide will explore everything you need to know about proxy servers: how they work, the different types available, their applications in various scenarios, and important considerations for their safe and effective use.
The Concept of Proxy Servers
At its core, a proxy server functions as a gateway between users and the internet. When you connect through a proxy:
- Your request is sent to the proxy server
- The proxy server forwards your request to the destination website
- The website sends the response back to the proxy server
- The proxy server relays that response back to you
This simple redirection has powerful implications. The destination website sees the request coming from the proxy server’s IP address, not yours. Meanwhile, your actual requests can be filtered, modified, cached, or otherwise processed by the proxy.
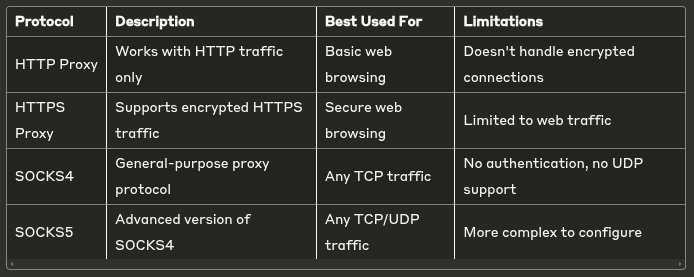
Common Proxy Protocols
Types of Proxy Servers
Forward Proxy:
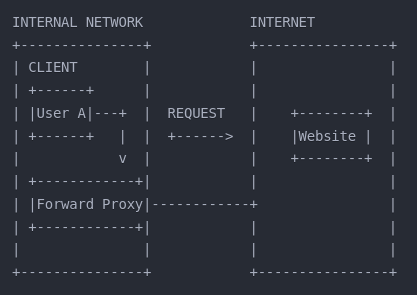
A forward proxy sits between clients and the internet, forwarding client requests to external websites. Organizations use this to provide internet access to internal networks while maintaining control.
Reverse Proxy:
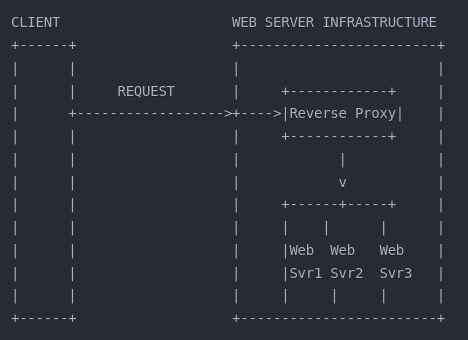
A reverse proxy sits in front of web servers, directing client requests to the appropriate backend server. Used for load balancing, security, and caching.
Transparent Proxy:
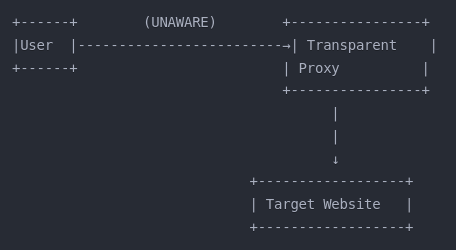
Users don’t know they’re using this proxy; it intercepts their traffic automatically. Commonly used for content filtering in corporate networks or public WiFi.
Anonymous Proxy:
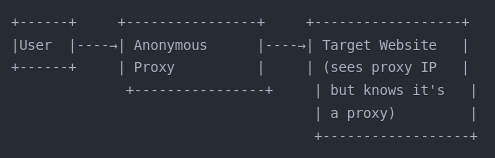
Identifies itself as a proxy but doesn’t reveal your identifying information. Provides basic anonymity but websites know a proxy is being used.
High-Anonymity Proxy:
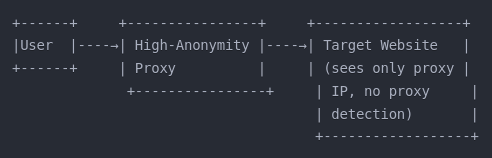
Doesn’t identify itself as a proxy and doesn’t pass your identifying information. Provides stronger anonymity than regular anonymous proxies.
Residential Proxy:
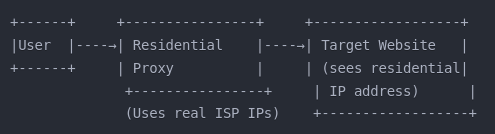
Uses IP addresses assigned to residential users by ISPs, making connections appear as regular home users rather than data centers.
Use Cases of Proxy Servers
🛡️ Content Filtering
- Schools restricting access to inappropriate content
- Companies blocking social media or non-work-related websites
- Parents implementing parental controls
🕵️ Anonymity and Privacy
- Hiding your IP address from websites
- Preventing tracking of your browsing habits
- Protecting identity when accessing sensitive information
⚖️ Load Balancing
- Distributing traffic across multiple servers
- Preventing server overload during high-traffic periods
- Ensuring website availability and reliability
⚡ Caching for Improved Performance
- Storing frequently accessed content locally
- Reducing bandwidth consumption
- Accelerating page load times
🌍 Bypassing Geo-Restrictions
- Accessing region-locked content
- Using services not available in your country
- Testing how websites appear in different regions
Enterprise Proxy Server Solutions
Organizations typically implement more robust proxy solutions than individual users. Here are some popular enterprise proxy servers:
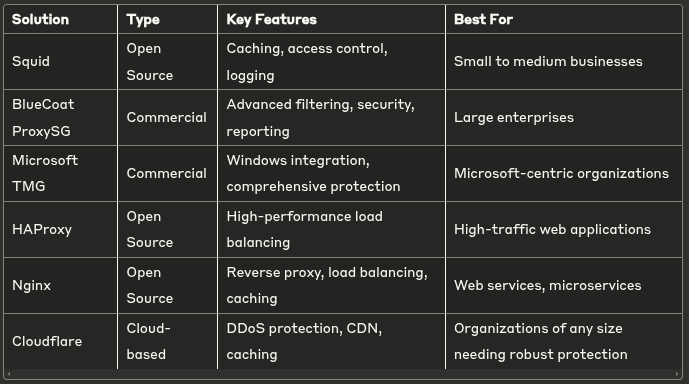
Spotlight on Squid: The Pioneer of Proxy Servers
One of the most iconic and widely used proxy servers in the early days of Linux is Squid. Developed as a caching and forwarding HTTP web proxy, Squid has been a staple in enterprise and educational environments for decades.
The Legacy and Evolution of Squid
- Linux Popularity: Squid gained traction on Linux systems due to its open-source nature and robust caching capabilities.
- Enterprise Use: Many organizations relied on Squid to manage bandwidth, reduce latency, and filter content.
- Innovations: While other companies have built modern proxy solutions, many still run on enhanced versions of Squid or have integrated its engine into their products.
Examples of tools based on or inspired by Squid:
- NetApp’s Blue Coat ProxySG
- Cisco’s Web Security Appliance
- Fortinet FortiProxy
Implementation considerations for businesses:
- Integration with existing security infrastructure
- Scalability requirements
- Compliance needs
- Performance impact
- Management and maintenance resources
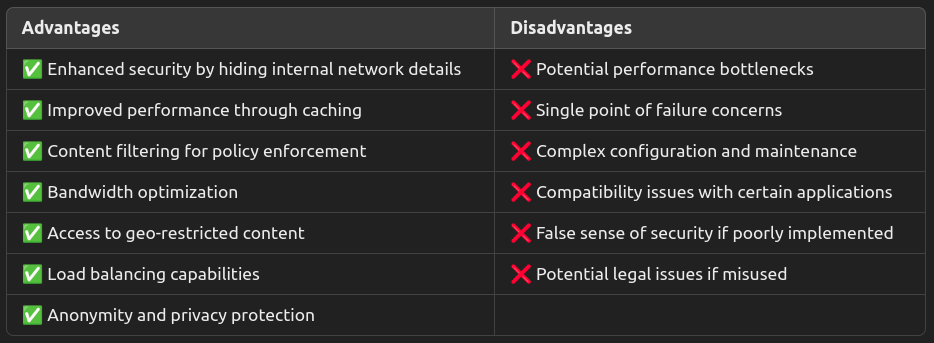
Advantages and Disadvantages of Proxy Servers
Public Proxy Servers Explained
Public proxies are servers that anyone can use, often without authentication. They come in several forms:
🆓 Free Public Proxies
- Available on various proxy listing websites
- Often unreliable and slow
- High turnover rate as they frequently go offline
- Typically have many simultaneous users
💰 Paid Public Proxy Services
- More reliable with better uptime
- Faster performance
- Better security practices
- Customer support available
Finding public proxies:
- Proxy listing websites
- Proxy service providers
- Search engines
- Online forums and communities
Safety Concerns with Public Proxies
⚠️ Security Risks
- Man-in-the-middle attacks
- Logging of your traffic and personal information
- Malware and malicious code injection
- Identity theft
⚠️ Anonymity Limitations
- Many don’t provide true anonymity
- Headers might still reveal identifying information
- Your ISP can still see that you’re using a proxy
⚠️ Data Privacy Issues
- Unencrypted connections expose your data
- Proxy operators can potentially see your traffic
- No guarantees about data handling practices
Proxy vs VPN
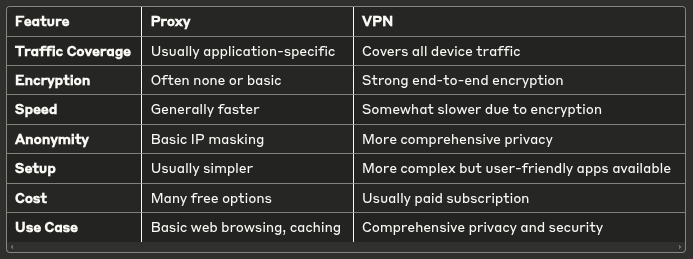
When to use a proxy:
- For simple IP masking needs
- When you only need to protect specific applications
- When speed is more important than security
- For caching and performance optimization
When to use a VPN:
- For comprehensive security on public Wi-Fi
- When privacy is a major concern
- When you need to protect all your traffic
- For stronger anonymity guarantees
Legal and Ethical Considerations
⚖️ Potential Legal Issues
- Using proxies for illegal activities doesn’t make you immune from prosecution
- Some countries restrict or ban proxy usage
- Accessing geo-restricted content may violate terms of service
📜 Compliance Concerns
- GDPR and data protection regulations
- Industry-specific compliance requirements
- Corporate security policies
🤔 Ethical Use
- Respecting website terms of service
- Avoiding excessive bandwidth consumption on shared proxies
- Being mindful of the impact on target servers
Security Best Practices for Proxy Users
🔒 Trust Verification
- Research proxy providers thoroughly
- Check reviews and reputation
- Verify privacy policies
🔐 Using Encryption
- Prefer HTTPS sites even when using proxies
- Consider using an encrypted proxy protocol
- Never send sensitive information through unencrypted connections
👁️ Monitoring and Auditing
- Regularly check proxy logs if available
- Monitor for unusual behavior
- Test proxy security periodically
Final Thoughts
Proxy servers are powerful tools that serve many purposes in our digital ecosystem. From enhancing privacy and security to optimizing network performance, they offer valuable benefits when properly implemented and used. However, it’s crucial to understand the limitations and risks associated with proxies, particularly public ones. The level of protection they provide depends greatly on the type of proxy, how it’s configured, and who operates it.
For casual use cases like bypassing simple geo-restrictions or basic anonymity, proxies may be sufficient. For more sensitive needs involving personal data or requiring stronger security guarantees, more comprehensive solutions like VPNs may be more appropriate. As with any technology tool, informed usage is key. By understanding the concepts covered in this guide, you’ll be better equipped to make smart choices about when and how to use proxy servers.




