In today’s digital world, web applications are the backbone of businesses, from e-commerce sites to internal management systems. But as their importance grows, so does the risk of cyberattacks. This is where Web Application Penetration Testing (WAPT) comes in – it’s a critical process to proactively find and fix security weaknesses before malicious attackers can exploit them.
What is Web Application Penetration Testing?
At its core, web application penetration testing is like a controlled, ethical hacking exercise. Skilled security professionals (called “penetration testers” or “ethical hackers”) simulate real-world attacks on a web application to identify vulnerabilities that could lead to data breaches, service disruptions, or other security incidents. Unlike automated scans, which are excellent for broad coverage, pen testing involves human intelligence and creativity to uncover complex flaws.
Why Are These Methodologies So Important?
You might wonder why we need a structured “methodology” for something that sounds like an art form. Here’s why:
- Comprehensive Coverage: A well-defined methodology ensures that all critical areas of a web application are systematically examined, reducing the chances of missing crucial vulnerabilities.
- Consistency and Repeatability: It provides a consistent framework, meaning tests can be performed and repeated with a clear process, leading to more reliable and comparable results over time.
- Efficiency: By following a logical sequence, pen testers can work more efficiently, prioritizing efforts where they are most needed and avoiding unnecessary steps.
- Meeting Compliance: Many industry regulations and standards (like PCI DSS for credit card processing or HIPAA for healthcare data) require regular penetration testing. A solid methodology helps meet these requirements.
- Adaptability: While there’s a standard process, it’s important to note that some phases can be scaled down or even omitted if they are not necessary or relevant to the specific application’s scope or risk profile. For instance, a very simple static website might not require extensive business logic testing. The methodology acts as a guide, not a rigid rulebook, allowing for flexibility based on the project’s unique needs.
- Clear Communication: A structured approach helps in clearly defining the scope, expectations, and reporting, ensuring everyone involved is on the same page.
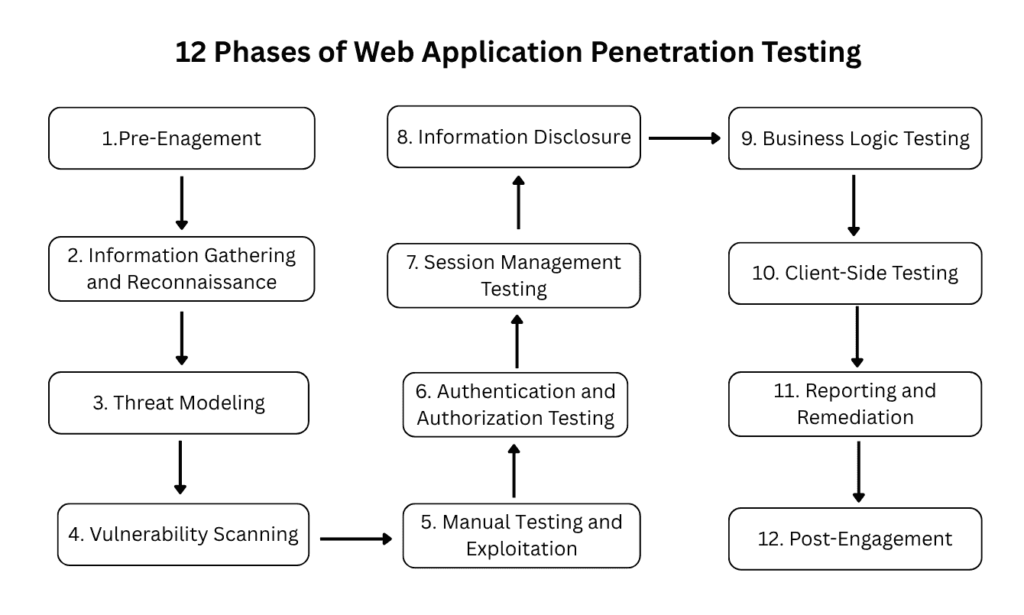
The 12 Phases of Web Application Penetration Testing
A typical web application penetration test follows a series of distinct, yet often overlapping, phases:
1. Pre-Engagement
This is the planning stage before any actual testing begins. It’s crucial for setting the groundwork.
- What happens: Defining the exact scope of the test (what’s in, what’s out), establishing rules of engagement (e.g., when testing can occur, what methods are allowed), signing legal agreements (like Non-Disclosure Agreements and consent forms), and setting up communication channels with the client.
- Why it matters: Prevents misunderstandings, sets clear boundaries, and ensures legal compliance.
2. Information Gathering and Reconnaissance
Before attacking, you need to understand your target. This phase is about collecting as much information about the application as possible.
- What happens: Gathering publicly available information (like domain names, IP addresses, employee details from social media), identifying technologies used (e.g., server type, programming languages, JavaScript frameworks), and mapping the application’s structure.
- Real-world example: Discovering a forgotten publicly accessible development server that contains sensitive configuration files.
- Tools involved: Public search engines, specialized browser extensions, and simple command-line tools.
3. Threat Modeling
Based on the gathered information, testers analyze potential threats to the application.
- What happens: Identifying potential attackers, understanding their motives, and brainstorming possible attack scenarios. This helps in prioritizing which areas of the application need the most rigorous testing.
- Real-world example: Realizing that a user profile update feature could be exploited by an attacker to change another user’s details if authorization controls are weak.
- Why it matters: It helps focus the testing efforts on the most critical risks and vulnerabilities.
4. Vulnerability Scanning
This phase uses automated tools to quickly identify common vulnerabilities.
- What happens: Running specialized software to scan the application for known weaknesses, such as outdated software versions or misconfigurations.
- Real-world example: A scanner might detect that a web server is running an old version known to have security flaws.
- Tools involved: Automated vulnerability scanners (sometimes called DAST – Dynamic Application Security Testing tools).
5. Manual Testing and Exploitation
This is where human ingenuity comes into play, going beyond what automated tools can find.
- What happens: Actively trying to exploit vulnerabilities manually. This includes trying to inject malicious code (e.g., SQL Injection to steal database information, Cross-Site Scripting or XSS to deface a webpage or steal user cookies), or trying to bypass input validations.
- Real-world example: Crafting a specific input that tricks the application into revealing sensitive user data from its database.
- Tools involved: Web proxies (like Burp Suite or OWASP ZAP) for intercepting and modifying traffic.
6. Authentication and Authorization Testing
This phase focuses on how users log in and what they are allowed to do.
- What happens: Testing for weak passwords, default credentials, flaws in the login process (e.g., ability to bypass multi-factor authentication), and checking if a user can access features or data they shouldn’t (e.g., a regular user accessing administrator functions, or viewing another user’s private data).
- Real-world example: A user changing a number in the website’s address bar to view another user’s order history (an “Insecure Direct Object Reference” or IDOR).
7. Session Management Testing
This phase examines how the application keeps track of a user’s session after they log in.
- What happens: Testing for predictable session tokens (which could allow an attacker to hijack a user’s session), improper session termination (e.g., remaining logged in indefinitely), and insecure cookie settings.
- Real-world example: An attacker guessing a user’s “session ID” and taking over their logged-in session.
8. Information Disclosure
This phase looks for instances where the application inadvertently reveals sensitive information.
- What happens: Checking for verbose error messages that expose database details, server paths, or internal logic; finding sensitive files left on the server (e.g., backup files, configuration files); or exposed API keys.
- Real-world example: An error message displaying the full path to a file on the server, which could help an attacker find other sensitive files.
9. Business Logic Testing
This is about understanding the application’s intended business processes and trying to subvert them.
- What happens: Testing for flaws in the application’s unique workflows. This could include manipulating pricing in an e-commerce cart, bypassing payment steps, or exploiting race conditions (where the timing of operations matters).
- Real-world example: Exploiting a flaw in a shopping cart that allows a user to buy an item for $0.01 instead of its actual price.
- Why it matters: These vulnerabilities are highly specific to the application and are almost impossible for automated tools to find.
10. Client-Side Testing
This phase focuses on vulnerabilities that primarily affect the user’s web browser.
- What happens: Testing for vulnerabilities like Cross-Site Request Forgery (CSRF), which tricks a user into performing an unintended action; Clickjacking, where an attacker overlays a transparent malicious page on top of a legitimate one; and insecure handling of data in the browser.
- Real-world example: An attacker sending a malicious link that, when clicked, automatically transfers money from the victim’s bank account (if they are logged in).
11. Reporting and Remediation
Once testing is complete, the findings are documented and communicated.
- What happens: A detailed report is generated, outlining each vulnerability found, its potential impact, a “proof of concept” (how it was exploited), and clear, actionable recommendations for fixing it. This often includes a risk rating (e.g., Critical, High, Medium, Low). The client then works to remediate these issues.
- Why it matters: The report is the primary deliverable; it guides the development team in fixing the identified flaws.
12. Post-Engagement
The final steps involve follow-up and wrapping up the engagement.
- What happens: This may include retesting fixed vulnerabilities to confirm they are indeed resolved, debriefing meetings with the client to discuss the findings and remediation strategy, and providing general security advice for future development.
- Why it matters: Ensures that the security posture has genuinely improved and maintains a good relationship for future engagements.
Our Key Takeaways
Web application penetration testing, guided by a robust methodology, is not just a checkbox exercise; it’s a vital component of a proactive cybersecurity strategy. Here are the key takeaways:
- It’s an Ongoing Process: The digital landscape is constantly changing, with new threats emerging regularly. Web applications also evolve. Therefore, security testing shouldn’t be a one-time event but rather a continuous, iterative process.
- Human Ingenuity is Key: While automated tools are helpful for initial scans, the real depth of a penetration test comes from the ethical hacker’s ability to think like an attacker and uncover complex, business-logic-driven flaws.
- It’s About Risk Management: Penetration testing helps organizations understand their security posture, identify their most critical risks, and prioritize their resources to address vulnerabilities effectively.
- Prevention is Better than Cure: Investing in regular and thorough penetration testing is significantly less costly and disruptive than dealing with the aftermath of a successful cyberattack.
By embracing these methodologies, organizations can build more resilient web applications, protect their data, and maintain the trust of their users.